Activities of "Theunis"
Hi,
My code created a file "Core.AlertNotification.json"
When I run the file I get "An error occured. : Object reference not set to an instance of an object." i.e. dotnet AspNetZeroRadTool.dll .\Core.AlertNotification.json
When I run any other.json file that has no Master detail , there is no issue.
Could you please reply to this ticket to ian@gofuseit.com
{ "IsRegenerate": true, "MenuPosition": "main", "RelativeNamespace": "Core", "EntityName": "AlertNotification", "EntityNamePlural": "AlertNotifications", "TableName": "AlertNotifications", "PrimaryKeyType": "int", "BaseClass": "Entity", "EntityHistory": false, "AutoMigration": true, "UpdateDatabase": false, "CreateUserInterface": true, "CreateViewOnly": true, "CreateExcelExport": false, "CreateExcelImport": false, "IsNonModalCRUDPage": false, "IsMasterDetailPage": true, "GenerateOverridableEntity": false, "GenerateUnitTest": false, "GenerateUiTest": false, "GenerateMobile": false, "PagePermission": { "Host": false, "Tenant": true }, "Properties": [ { "Name": "DateOccured", "Type": "DateTime", "MaxLength": -1, "MinLength": -1, "Range": { "IsRangeSet": false, "MinimumValue": 0.0, "MaximumValue": 0.0 }, "Required": false, "Nullable": false, "Regex": "", "IsMultiLingual": false, "UserInterface": { "AdvancedFilter": true, "List": true, "ListMaui": false, "CreateOrUpdate": false }, "ViewType": null, "AdditionalData": {} }, { "Name": "AlertRead", "Type": "bool", "MaxLength": -1, "MinLength": -1, "Range": { "IsRangeSet": false, "MinimumValue": 0.0, "MaximumValue": 0.0 }, "Required": false, "Nullable": false, "Regex": "", "IsMultiLingual": false, "UserInterface": { "AdvancedFilter": true, "List": true, "ListMaui": false, "CreateOrUpdate": false }, "ViewType": null, "AdditionalData": {} }, { "Name": "DateLastModified", "Type": "DateTime", "MaxLength": -1, "MinLength": -1, "Range": { "IsRangeSet": false, "MinimumValue": 0.0, "MaximumValue": 0.0 }, "Required": false, "Nullable": false, "Regex": "", "IsMultiLingual": false, "UserInterface": { "AdvancedFilter": true, "List": true, "ListMaui": false, "CreateOrUpdate": false }, "ViewType": null, "AdditionalData": {} }, { "Name": "Latitude", "Type": "double", "MaxLength": -1, "MinLength": -1, "Range": { "IsRangeSet": false, "MinimumValue": 0.0, "MaximumValue": 0.0 }, "Required": false, "Nullable": false, "Regex": "", "IsMultiLingual": false, "UserInterface": { "AdvancedFilter": false, "List": true, "ListMaui": false, "CreateOrUpdate": true }, "ViewType": null, "AdditionalData": {} }, { "Name": "Longitude", "Type": "double", "MaxLength": -1, "MinLength": -1, "Range": { "IsRangeSet": false, "MinimumValue": 0.0, "MaximumValue": 0.0 }, "Required": false, "Nullable": false, "Regex": "", "IsMultiLingual": false, "UserInterface": { "AdvancedFilter": false, "List": true, "ListMaui": false, "CreateOrUpdate": true }, "ViewType": null, "AdditionalData": {} }, { "Name": "AlertValue", "Type": "string", "MaxLength": -1, "MinLength": -1, "Range": { "IsRangeSet": false, "MinimumValue": 0.0, "MaximumValue": 0.0 }, "Required": false, "Nullable": false, "Regex": "", "IsMultiLingual": false, "UserInterface": { "AdvancedFilter": false, "List": true, "ListMaui": false, "CreateOrUpdate": true }, "ViewType": null, "AdditionalData": {} }, { "Name": "FullStreetName", "Type": "string", "MaxLength": -1, "MinLength": -1, "Range": { "IsRangeSet": false, "MinimumValue": 0.0, "MaximumValue": 0.0 }, "Required": false, "Nullable": false, "Regex": "", "IsMultiLingual": false, "UserInterface": { "AdvancedFilter": true, "List": true, "ListMaui": false, "CreateOrUpdate": true }, "ViewType": null, "AdditionalData": {} }, { "Name": "Roadspeed", "Type": "int", "MaxLength": -1, "MinLength": -1, "Range": { "IsRangeSet": false, "MinimumValue": 0.0, "MaximumValue": 0.0 }, "Required": false, "Nullable": false, "Regex": "", "IsMultiLingual": false, "UserInterface": { "AdvancedFilter": false, "List": true, "ListMaui": false, "CreateOrUpdate": true }, "ViewType": null, "AdditionalData": {} }, { "Name": "DriverId", "Type": "int", "MaxLength": -1, "MinLength": -1, "Range": { "IsRangeSet": false, "MinimumValue": 0.0, "MaximumValue": 0.0 }, "Required": false, "Nullable": false, "Regex": "", "IsMultiLingual": false, "UserInterface": { "AdvancedFilter": true, "List": true, "ListMaui": false, "CreateOrUpdate": true }, "ViewType": null, "AdditionalData": {} }, { "Name": "DriverFirstName", "Type": "string", "MaxLength": 250, "MinLength": 0, "Range": { "IsRangeSet": false, "MinimumValue": 0.0, "MaximumValue": 0.0 }, "Required": false, "Nullable": true, "Regex": "", "IsMultiLingual": false, "UserInterface": { "AdvancedFilter": true, "List": true, "ListMaui": false, "CreateOrUpdate": true }, "ViewType": null, "AdditionalData": {} }, { "Name": "DriverLastName", "Type": "string", "MaxLength": 250, "MinLength": 0, "Range": { "IsRangeSet": false, "MinimumValue": 0.0, "MaximumValue": 0.0 }, "Required": false, "Nullable": true, "Regex": "", "IsMultiLingual": false, "UserInterface": { "AdvancedFilter": true, "List": true, "ListMaui": false, "CreateOrUpdate": true }, "ViewType": null, "AdditionalData": {} }, { "Name": "DriverTag", "Type": "string", "MaxLength": 250, "MinLength": 0, "Range": { "IsRangeSet": false, "MinimumValue": 0.0, "MaximumValue": 0.0 }, "Required": false, "Nullable": true, "Regex": "", "IsMultiLingual": false, "UserInterface": { "AdvancedFilter": true, "List": true, "ListMaui": false, "CreateOrUpdate": true }, "ViewType": null, "AdditionalData": {} }, { "Name": "RegistrationNumber", "Type": "string", "MaxLength": 250, "MinLength": 0, "Range": { "IsRangeSet": false, "MinimumValue": 0.0, "MaximumValue": 0.0 }, "Required": false, "Nullable": true, "Regex": "", "IsMultiLingual": false, "UserInterface": { "AdvancedFilter": true, "List": true, "ListMaui": false, "CreateOrUpdate": true }, "ViewType": null, "AdditionalData": {} }, { "Name": "Imei", "Type": "string", "MaxLength": 250, "MinLength": 0, "Range": { "IsRangeSet": false, "MinimumValue": 0.0, "MaximumValue": 0.0 }, "Required": false, "Nullable": true, "Regex": "", "IsMultiLingual": false, "UserInterface": { "AdvancedFilter": true, "List": true, "ListMaui": false, "CreateOrUpdate": true }, "ViewType": null, "AdditionalData": {} }, { "Name": "AlertIdentifier", "Type": "string", "MaxLength": 50, "MinLength": 0, "Range": { "IsRangeSet": false, "MinimumValue": 0.0, "MaximumValue": 0.0 }, "Required": false, "Nullable": true, "Regex": "", "IsMultiLingual": false, "UserInterface": { "AdvancedFilter": true, "List": true, "ListMaui": false, "CreateOrUpdate": true }, "ViewType": null, "AdditionalData": {} } ], "NavigationProperties": [ { "Namespace": "ITS.Core", "ForeignEntityName": "Device", "ForeignEntityNamePlural": "Devices", "IdType": "int", "IsNullable": true, "PropertyName": "DeviceId", "DuplicationNumber": 0, "RelationType": "single", "ViewType": "LookupTable", "DisplayPropertyNameInfos": { "MergeFormat": "{0}", "DisplayPropertyNames": [ "IMEI" ] } }, { "Namespace": "ITS.Core", "ForeignEntityName": "AlertType", "ForeignEntityNamePlural": "AlertTypes", "IdType": "int", "IsNullable": true, "PropertyName": "AlertTypeId", "DuplicationNumber": 0, "RelationType": "single", "ViewType": "LookupTable", "DisplayPropertyNameInfos": { "MergeFormat": "{0}", "DisplayPropertyNames": [ "AlertDescription" ] } } ], "NavigationPropertyOneToManyTables": [ { "EntityJson": "Core.AlertComment.json", "ForeignPropertyName": "AlertNotificationId", "IsNullable": true, "DisplayPropertyName": "", "ViewType": "LookupTable" } ], "EnumDefinitions": [], "DbContext": null }
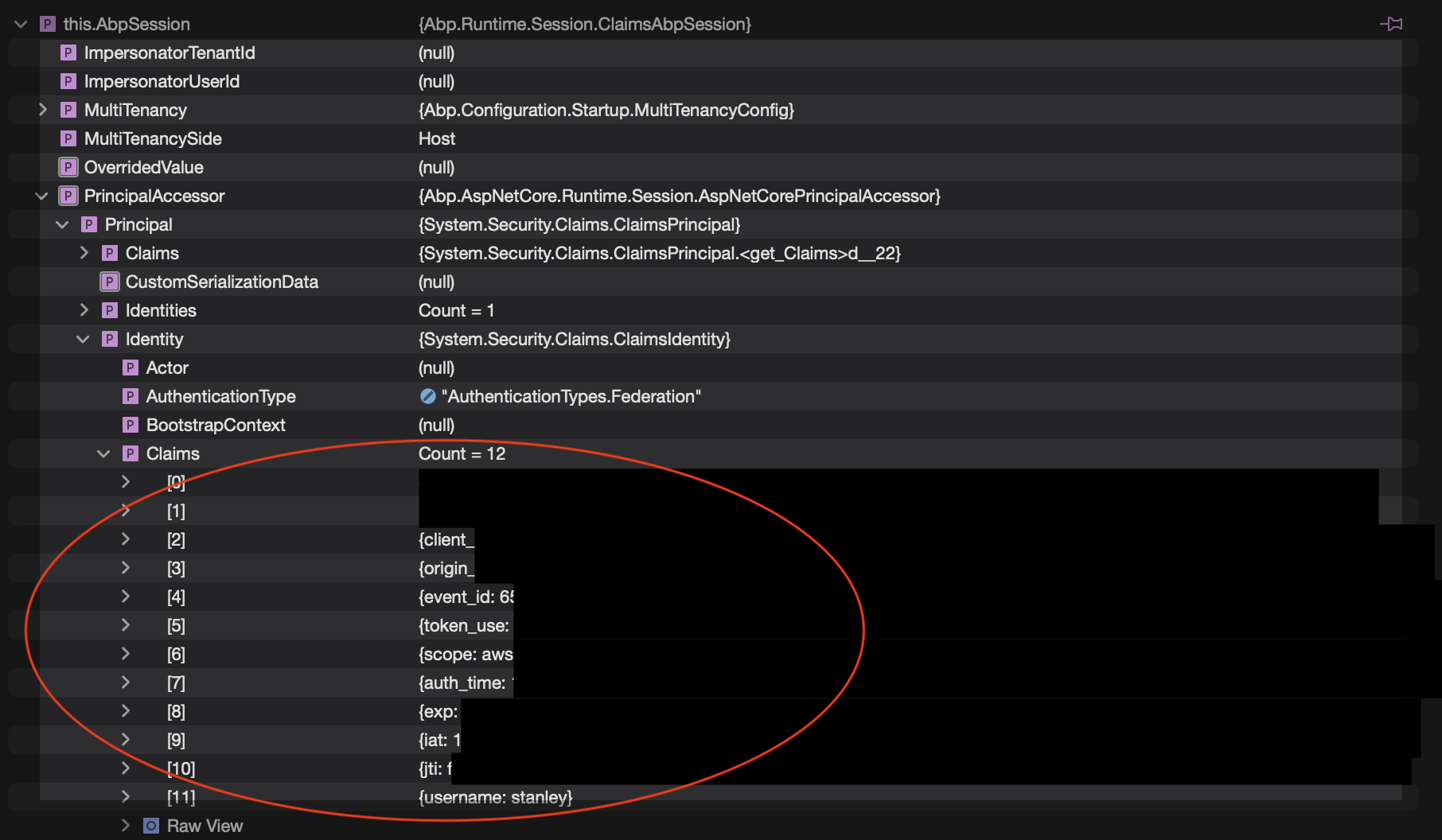
We are using ASP.NET Zero and we want to use AWS Cognito as Authentication Provider. We are using Cognito to authenticate on Mobile Apps and we also aim to use Cognito to authenticate on the Angular ASP.Net Zero Web Application. Thus, we want to authenticate against a Cognito JWT Access Token in our Application Services as well as our Controllers. I have added JWT Token validation in the Web.Host project and I have decorated the Application Service class with the [Authorize] attribute. When I make a call to the API with a valid JWT token from Cognito I am able to access the service whereas if I have an invalid token I get a 401 Unauthorized error. So the authorization and token validation works nicely as expected. However, I am now trying to identify the user within the Application Service and I am unable to do so. If I set a breakpoint inside the method in the Application Service I can see that the PrincipalAccessor contains the claims from the JWT token. The Principal Accessor isn't accessible from the Application Service though so I don't have a means of reading it. When I try to read a user identifier I also get null values and if I use GetCurrentUser() I get an exception that Session.UserId is null.
I have two questions:
- How can I get access to the claims from within the Application Service?
- I assume that there is a better way of achieving Cognito Authentication where, after I've validated the JWT token I probably perform some ABP magic to create an Abp Session such that all Application Services and Controllers can use the AbpSession just like they normally would, oblivious to the fact that the identity or the authentication actually came from AWS Cognito rather than ABP's built-in authentication mechanism. But I have no idea how to achieve this? How should AWS Cognito Authentication be implemented appropriately?
This is my code in my Application Service:
public class HelloWorldAppService : ITSAppServiceBase, IHelloWorldAppService
{
[Authorize]
public HelloWorldDto GetAll()
{
var temp = this.AbpSession.ToString();
var id = this.AbpSession.ToUserIdentifier(); //id is null
//var u = this.GetCurrentUser(); //method throws an exception: Session.UserId is null! Probably, user is not logged in.
return new HelloWorldDto() { Message = "Hello world!"};
}
}
This is the content of AbpSession when I set a breakpoint in the method in the Application Service:
This is the extension we have added in our Web.Host project to validate the JWT token:
` public static IServiceCollection AddAwsCognitoAuthentication(this IServiceCollection services, AppSettings appSettings) {
services.AddAuthentication(options => {
options.DefaultAuthenticateScheme = JwtBearerDefaults.AuthenticationScheme;
options.DefaultSignInScheme = JwtBearerDefaults.AuthenticationScheme;
options.DefaultChallengeScheme = JwtBearerDefaults.AuthenticationScheme;
})
.AddJwtBearer(options => {
options.ClaimsIssuer = CognitoIssuer;
options.SaveToken = true;
options.TokenValidationParameters = new TokenValidationParameters() {
ValidateLifetime = true,
ValidateIssuerSigningKey = true,
IssuerSigningKeyResolver = (s, securityToken, identifier, parameters) => {
// get JsonWebKeySet from AWS
var json = new WebClient().DownloadString(CognitoIssuer + "/.well-known/jwks.json");
// serialize the result
var keys = JsonConvert.DeserializeObject<JsonWebKeySet>(json).Keys;
// cast the result to be the type expected by IssuerSigningKeyResolver
return keys;
},
ValidateIssuer = true,
ValidIssuer = CognitoIssuer,
ValidateAudience = false,
};
options.Events = new JwtBearerEvents() {
//Code omitted for brevity
};
});
return services;
}`
and we are calling this extension in Startup.cs:
services.AddAwsCognitoAuthentication(_appSettings);