I followed the directions carefully on how to upgrade an existing project. I downloaded version 12.2.1 in the same configuration as my original project and put it in the aspnetzero branch. Firth thing I noticed was that the version number listed everywhere was "12.2.0", not "12.2.1" - Is this a problem?
Next, I resolved all merge and build issues with both the client and the server. Next, I ran the server, and it started up fine, then I ran the angular client with "npm run hmr" and it started fine.
Next, I was able to navigate to the login page. I attempted to log into the host with 2FA disabled for now.
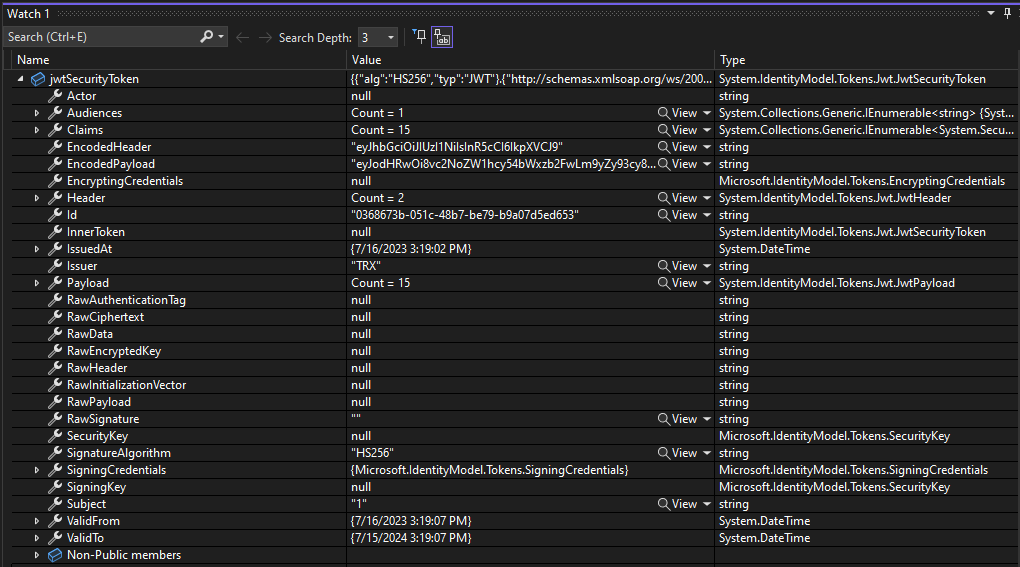
The actual login appears to work, but it then fails in the TokenAuthController's CreateToken method.
I have included a screenshot of the token that is produced below.
Additionally, the actual failure occurs at line 864 in TokenAuthController.cs
return new JwtSecurityTokenHandler().WriteToken(jwtSecurityToken);
And the error produced is:
IDX10720: Unable to create KeyedHashAlgorithm for algorithm 'HS256', the key size must be greater than: '256' bits, key has '160' bits. (Parameter 'keyBytes')
I have a lot riding on this working quickly. Can somebody point me to what they think may be wrong?
Many thanks for your time and effort. Gerry
4 Answer(s)
-
0
-
0
@m.aliozkaya Thank you so much for your response. I really appreciate it.
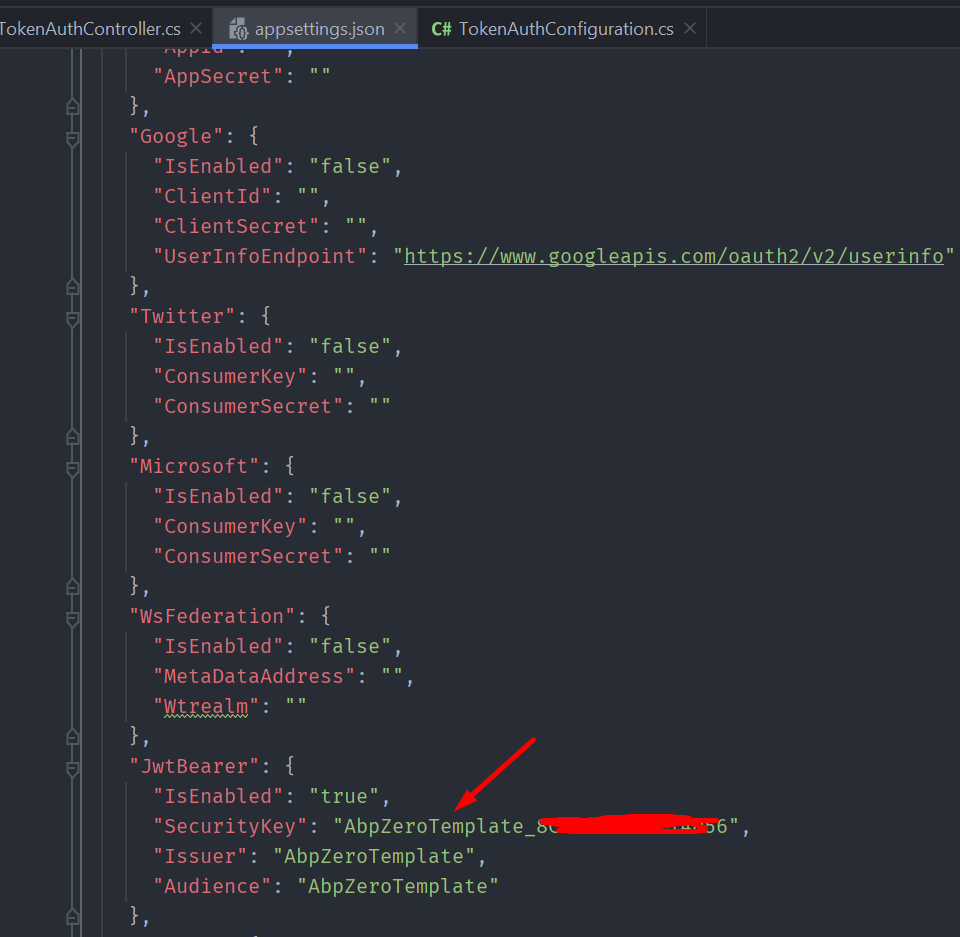
Making the JwtBearer.SecurityKey longer did change where the issue is occurring; I just arbitrarily added a random 12 character string; 11 characters repeated the previous behavior, and 12 characters allowed it to succeed to the next failure. Since that was the default token that the template was generated with, i'm guessing this will be a problem for others. Did the hash key size change?
Now when the loginService eventually calls the ZeroRefreshTokenService, it invokes the tryAuthWithRefreshToken(). Within that method it calls getRefreshToken() which fails, and causes the redirect to the internal pages to fail.
Any insight would be much appreciated, especially why I had to make any changes at all to the SecurityKey length.
Many thanks, Gerry
p.s. I went to my aspnetzero branch which contained the newly downloaded project and created a new database and ran the project. Login was still broken. I also noticed that much of the client authentication/JWT code was refactored over the last release. Any chance i'm hitting a framework issue and not a bad merge/upgrade?
-
0
Hi @gerryp,
The HmacSha256 in the line SigningCredentials(signinKey, SecurityAlgorithms.HmacSha256) should be greater than 128 bits. In short, use a long string as the key.
I tested the issue in a new project but it seems correct. Could you check your upgraded project maybe the problem is elsewhere?
-
0
M. Thanks for looking at this. I figured out the problem.
In my project XXX.Web.Core I left around the Microsoft.IdentityModel.xxxx packages. Those were replaced with some other packages, but it still allowed the project to build, making me think they were previously used versions of the package. Anyway, once i went through the solution, project by projects and compared the Packages I was able to find the problem. No lengthening of the SecurityToken was necessary.
Just a warning to all people performing upgrades: Carefully check the packages and versions for each project in the solution against the new downloaded version.
Thanks, Gerry