I'm confused as to why we don't have access to the source code for Abp.AspNetZeroCore.Web. Shouldn't that source be available in one of the private repo's in https://github.com/aspnetzero? If we have an active license don't we have access to the source code?
What am I misunderstanding?
reference other posts about this topic:
https://support.aspnetzero.com/QA/Questions/4571#answer-86b1a766-de44-49d6-aa29-fa0f014f9e5d
yeah this package is closed source due to licensing purposes.
and https://support.aspnetzero.com/QA/Questions/8511/Access-to-the-AbpAspNetZeroCoreWeb
8 Answer(s)
-
0
Hi @mdepouw
This library contains license control code and because of that, it is close sourced, see https://aspnetzero.com/Faq#provides-full-source-code. If you need to access business code in this library, please send an email to [email protected]
-
0
Hi @ismcagdas 👋
- The solution also has a closed-source NuGet package that is used to protect ASP.NET Zero's license rules. source
That part makes sense 👍. If the source was available for license checking then one could subvert the rules & modify that code. But, anything outside of that, why make that closed source? 🤔
For example, I'm extending ASP.NET Zero to support multiple OpenID providers in one tenant & I wanted to understand how
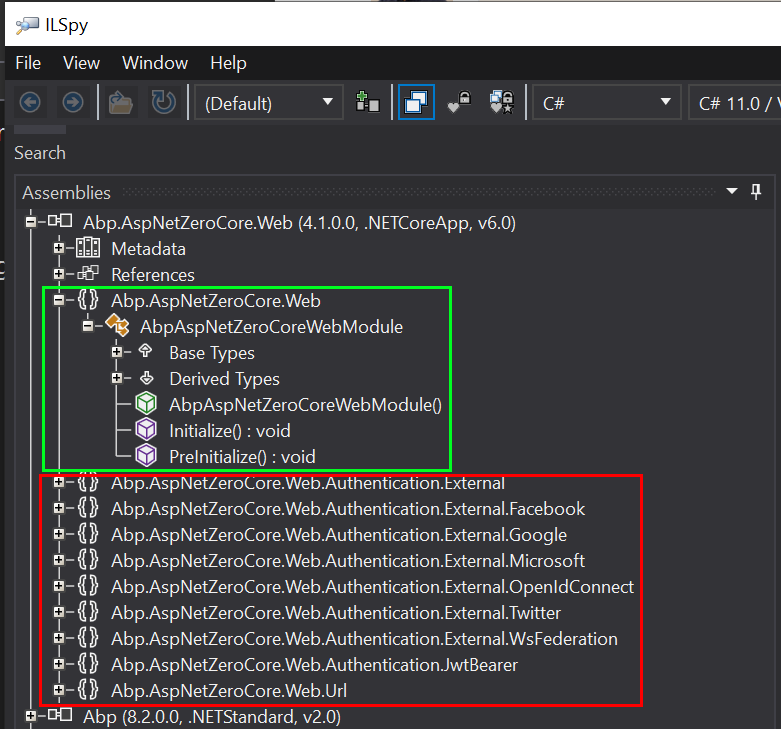
Abp.AspNetZeroCore.Web.Authentication.External.ExternalAuthManageris behaving.Please see the screenshot below... the green I get & is properly related to licensing but the red, how does that related to licensing? 🤔
Not a huge deal, just trying to understand 😊, thanks!
-
0
Hi,
Thanks :).
ExternalAuthManagercurrently supports only one OIDC provider. It basically creates an externalpublic IDisposableDependencyObjectWrapper<IExternalAuthProviderApi> CreateProviderApi(string provider) { ExternalLoginProviderInfo providerInfo; if (_externalAuthConfiguration.ExternalLoginInfoProviders.Any(infoProvider => infoProvider.Name == provider)) { providerInfo = _externalAuthConfiguration.ExternalLoginInfoProviders .Single(infoProvider => infoProvider.Name == provider) .GetExternalLoginInfo(); } else // if not exist in new version, use old one { providerInfo = _externalAuthConfiguration.Providers.FirstOrDefault(p => p.Name == provider); } if (providerInfo == null) { throw new Exception("Unknown external auth provider: " + provider); } var providerApi = _iocResolver.ResolveAsDisposable<IExternalAuthProviderApi>(providerInfo.ProviderApiType); providerApi.Object.Initialize(providerInfo); return providerApi; }For OIDC, it uses
OpenIdConnecttext. So, you may create a new OIDC provider withOpenIdConnect2for example to support second OIDC provider. -
0
So, you may create a new OIDC provider with OpenIdConnect2 for example to support second OIDC provider.
That's the path I was heading down 😊! The issue I came across when doing that was on
ExternalAuthManager.GetUserInfo(). The provider is not passed through toOpenIdConnectAuthProviderApi.GetUserInfo().In the returned object, I can see the Provider is hardcoded 😢. I ended up overriding the
Providerafter calling the method. i.e.var userInfo = await _externalAuthManager.GetUserInfo(model.AuthProvider, model.ProviderAccessCode); // ugly! userInfo.Provider = model.AuthProvider; return userInfo;Decompiled code snippet of
OpenIdConnectAuthProviderApi:public class OpenIdConnectAuthProviderApi : ExternalAuthProviderApiBase { public override async Task<ExternalAuthUserInfo> GetUserInfo(string token) { ... return new ExternalAuthUserInfo { Provider = "OpenIdConnect", ProviderKey = validatedTokenResult.Token.Subject, Name = fullNameParts[0], Surname = ((fullNameParts.Length > 1) ? fullNameParts[1] : fullNameParts[0]), EmailAddress = emailClaim.Value, Claims = validatedTokenResult.Principal.Claims.Select((Claim c) => new ClaimKeyValue(c.Type, c.Value)).ToList() }; } } -
0
Please see the screenshot below... the green I get & is properly related to licensing but the red, how does that related to licensing? 🤔
My question still stands though 😊
-
0
Next challenge, how can I add additional configuration fields to an OpenID Connect provider if that source code is not modifiable?
I wanted to add
IssuerandWellKnowntoappsettings.jsonfor supporting Azure AD B2C but I'm not seeing a way w/o hacking up the code. Seems like a pretty simple thing, add a few more fields to the config & modify the code that's reading it but that's not the case here.I'm not seeing it, what does "license control code" have to do w/ external authentication? 🤔
-
0
Please see the screenshot below... the green I get & is properly related to licensing but the red, how does that related to licensing? 🤔
These are the code blocks we selected to put into license control package. If license control pacakge doesn't have any source code used in the main app, so you can easily delete the reference of license packages and disable license control :)
Authorityin the appsettings.json is used as theIssuer. I'm not sure why do you needWellKnown.Did you configure
OpenIdsection in appsettings.json and faced a problem while login via Azure AD ? -
0
If license control pacakge doesn't have any source code used in the main app, so you can easily delete the reference of license packages and disable license control :)
Ah, 🤦♂️, that makes sense! I see now, thanks!
Did you configure OpenId section in appsettings.json and faced a problem while login via Azure AD ?
I did but we're using Azure AD B2C not AD 😊. Please see this ticket for challenges (looks like lack of support) for configuring Zero w/ B2C.
Closing this ticket, thanks!