Hi, Our application is failed in VAPT test for, Cryptographic failure - Password sent in Clear text format
Check below details:
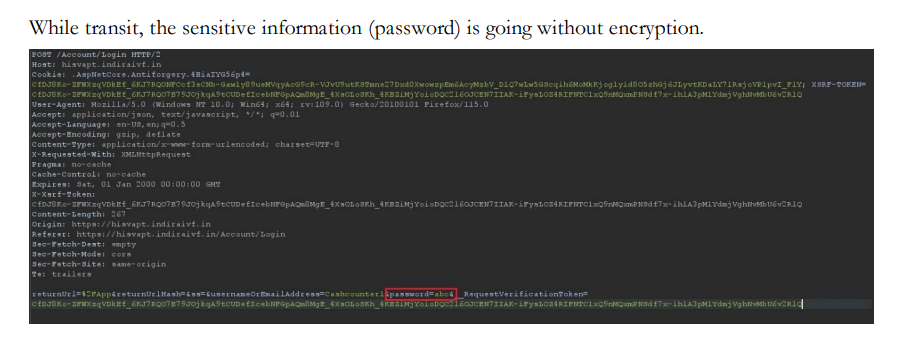
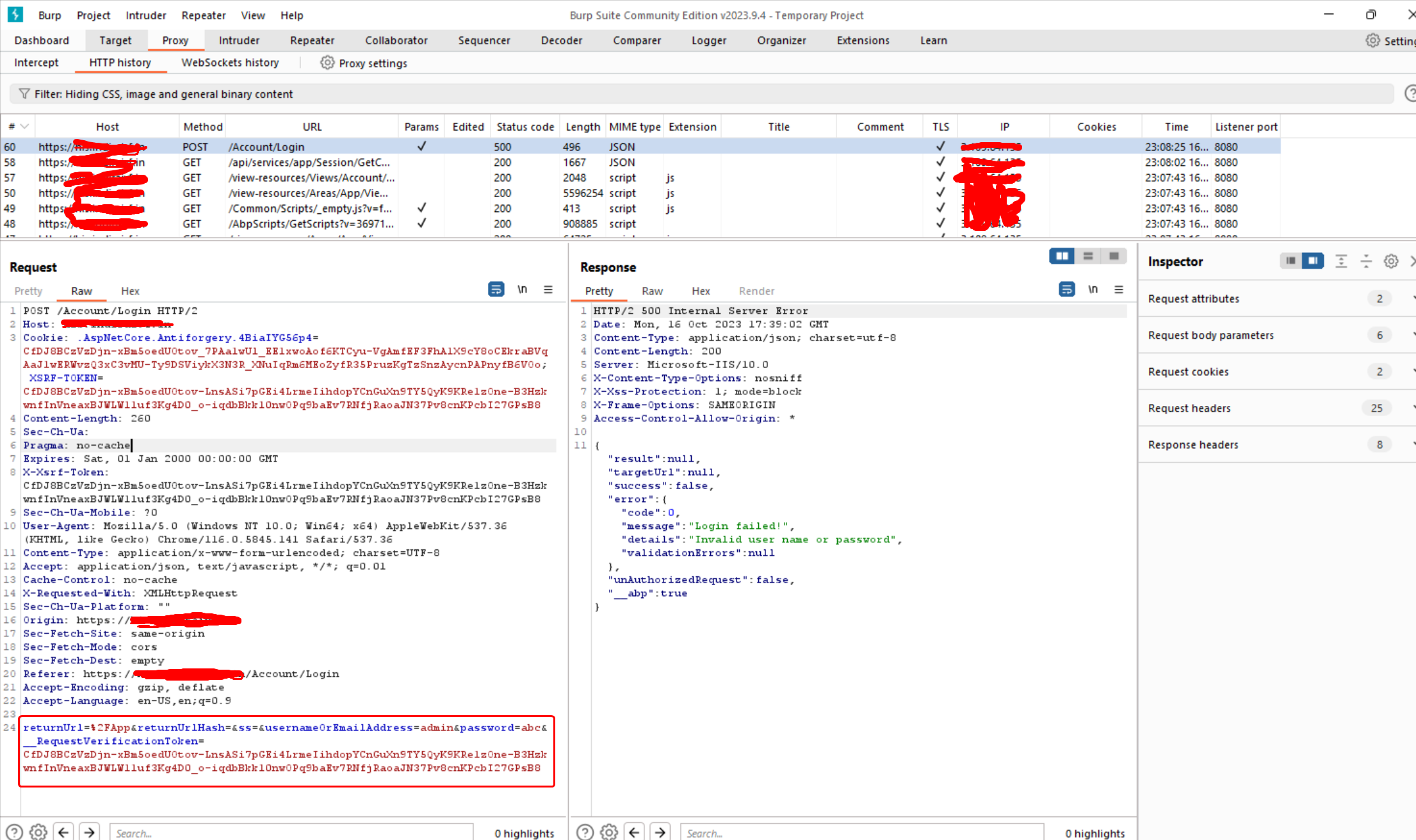
**Threat Description: ** The pathway of sensitive data like passwords is reflected in plain texts which leads the intruders to get these details by capturing the HTTP requests either using from wire shark or burp suite or any malicious attempts. Impact: A third-party attacker is able to read the user credentials like passwords by intercepting a connection. Evidence: In the below screen shot, we will intercept and capture the login username and password request in Burpsuite.
Recommendations: • It is recommended to use strong encryption algorithm like SHA512 to encrypt sensitive data in transit. • All sensitive parameters must be encrypted using strong algorithm
Please provide the solution for this test, while login the application
5 Answer(s)
-
0
Hi @kansoftware
Since we suggest using HTTPS, we won't implement such a feature. Also, what is the point of encrypting the password on the client side ? I think there shouldn't be such an encrption on the client side app.
-
0
Hi
Actually, this was reported by our team working on VAPT for our EMR application which we built using ASPNETZERO, We have observed client side encryption on some of the banking websites.
Can you please help how we can answer VAPT team for this issue. So, they can close this issue
Regards, Harshit
-
0
Hi @kansoftware
I think I got the problem wrong at first but when I look at the screenshot, I see the password on querystring. Is it possible to share the steps to reproduce this case ?
-
0
Hi,
We are trying to intercept the request using a Burp suite Tool
- Install Burpsuite community edition
- Select Proxy option
- Enable intecept on
- Open browser from burpsuite
- Open Aspnetzero application login page
- enter username and password
- you will see a post request as in screenshot
Let us know if you need any further assistance.
Regards Harshit
-
0
Hi,
Thanks, I got it now. Since you are using HTTPS, communication between client and server is encrpted. So, I guess you don't want to worry about this. See item 5 under "How to Prevent" title in https://owasp.org/Top10/A02_2021-Cryptographic_Failures/