ASP.NET CORE MVC & jQuery: v13.3.0
.NET 8
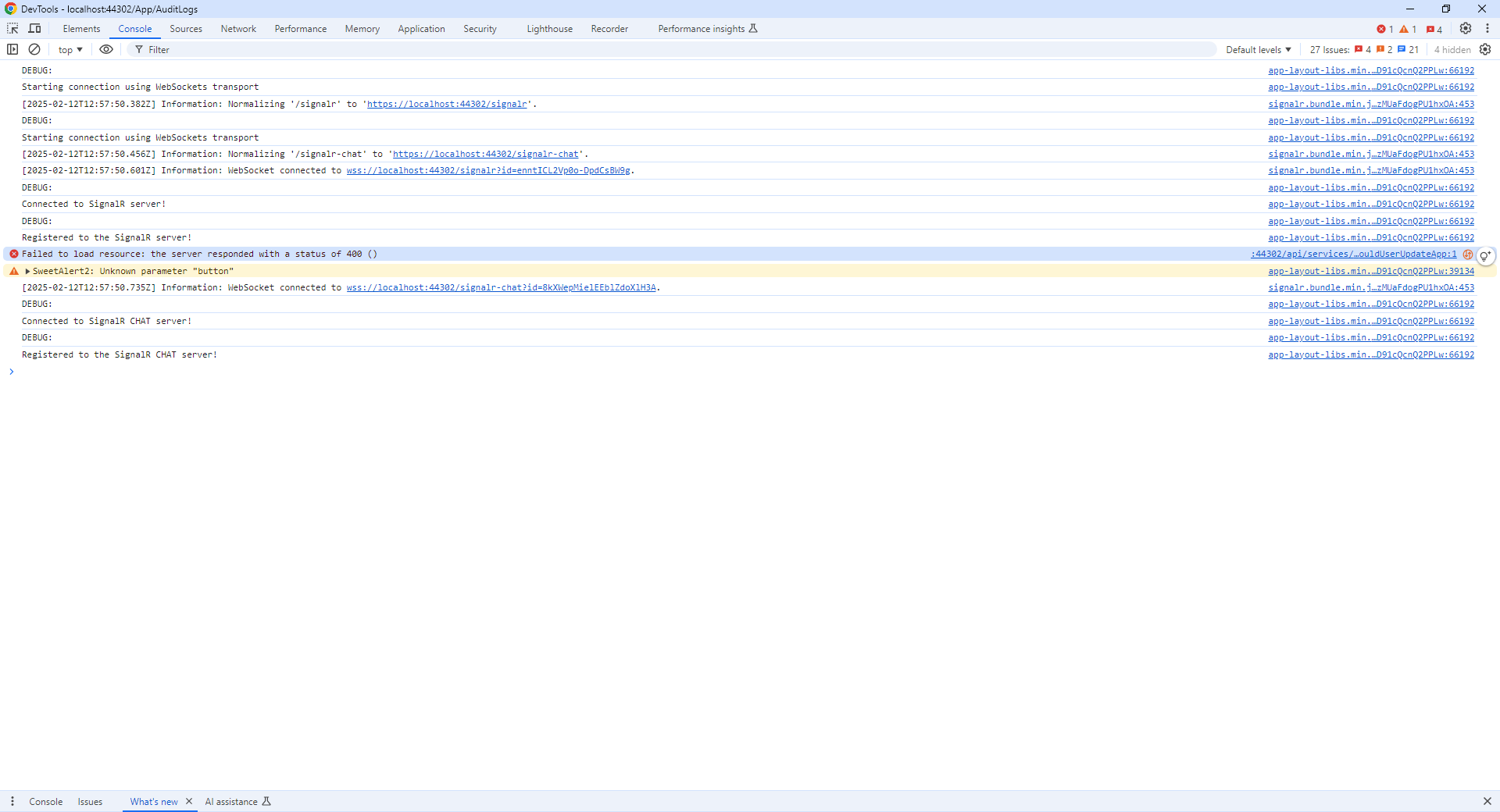
Adding HTTP-Only to the XSRF-TOKEN cookie results in 400 (Bad Request) errors throughout the application.
Followed "HTTP-Only Anti-Forgery Token in ASP.NET Zero" blog. https://aspnetzero.com/blog/http-only-anti-forgery-token-in-asp.net-zero..
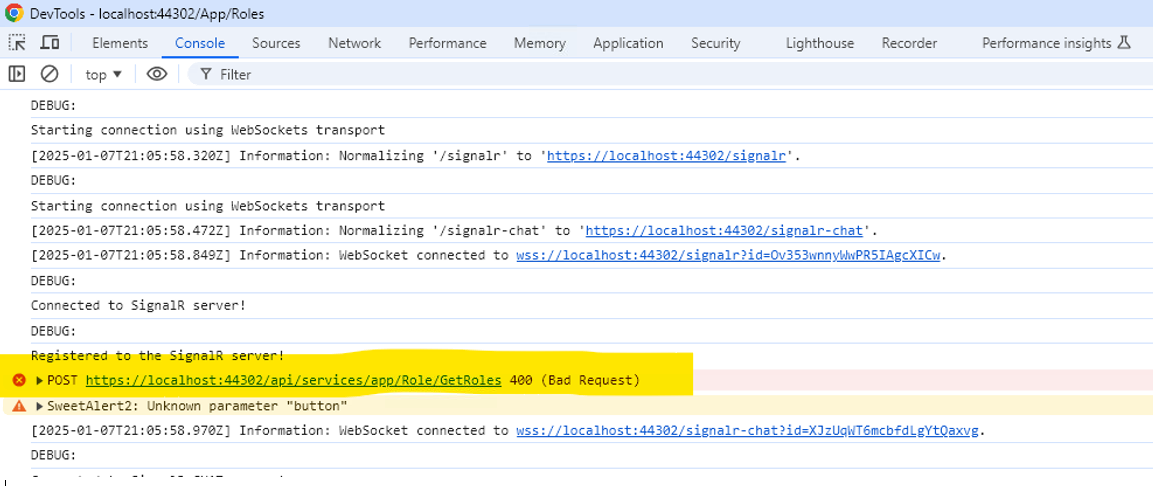
Attached is a screenshot from DevTools with a service call. All calls throughout the application result in a 400 (Bad Request) error.
13 Answer(s)
-
0
Hi @truist.software,
Can you share your request network and the cookies?
-
0
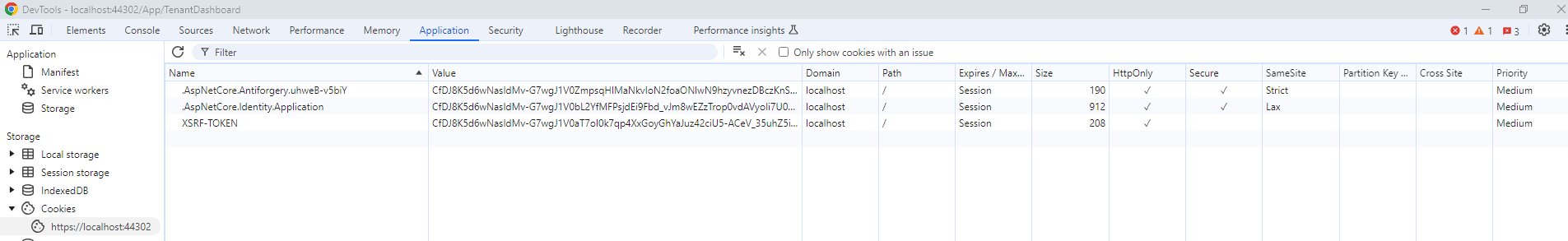
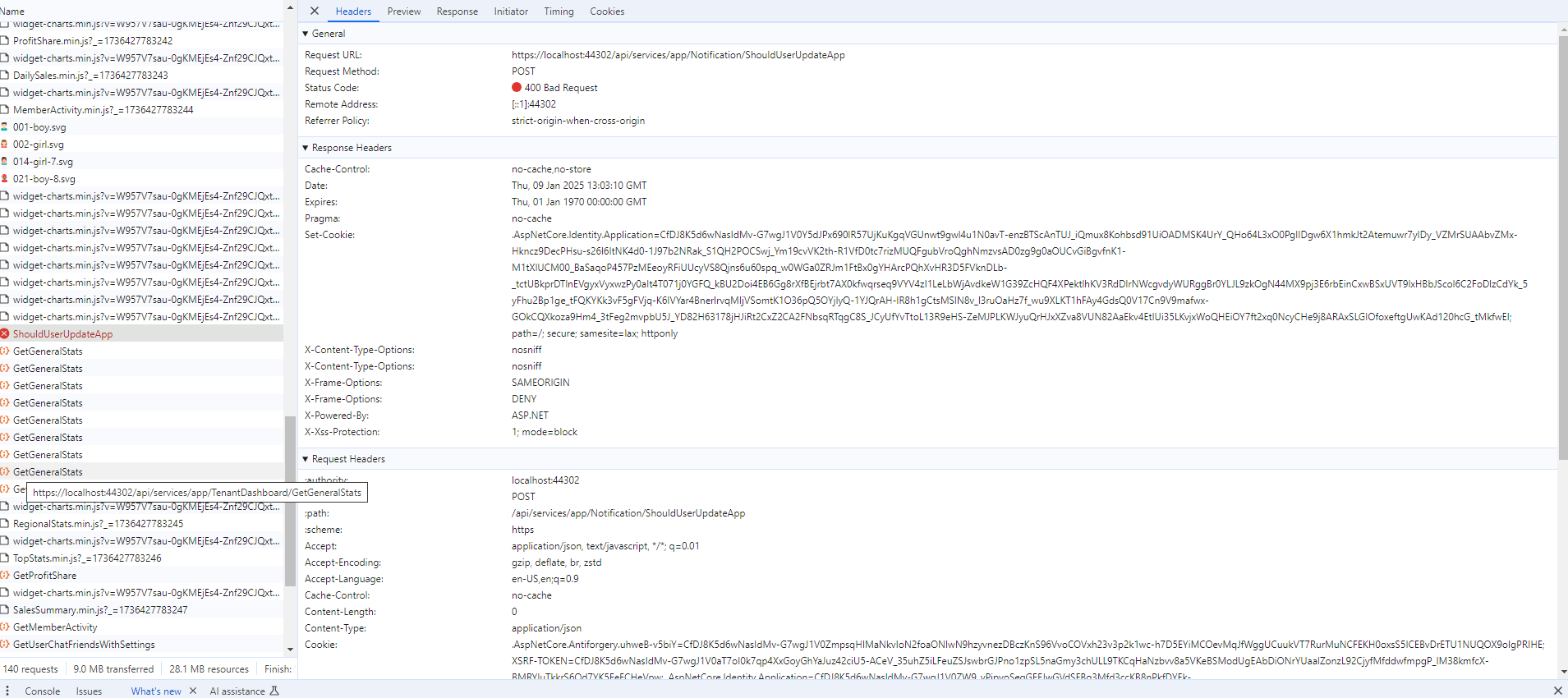
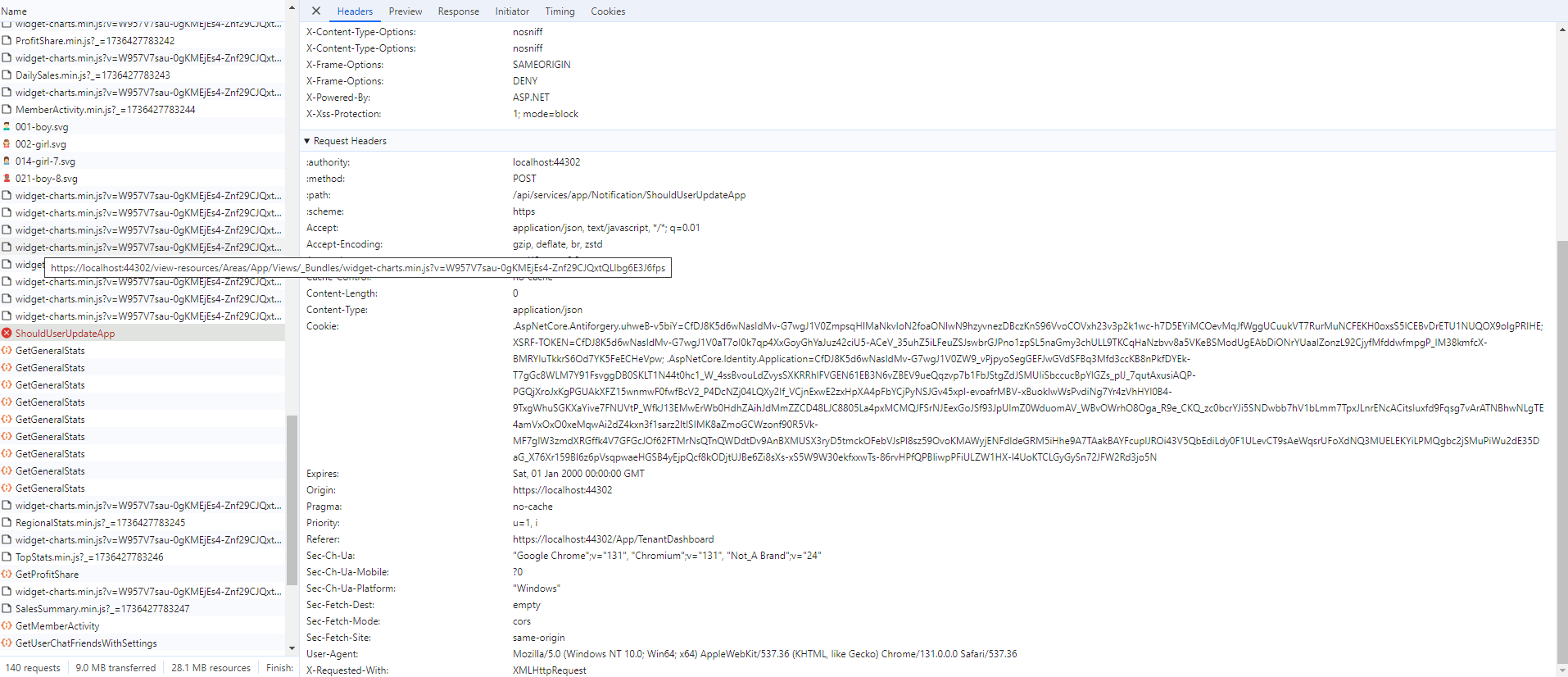
Updated with Cookies and Network information.
-
0
Hi @truist.software,
Do you have a cookie like this?

You may also have forgotten about using middleware.

-
0
As the screenshots show I do have the XSRF-TOKEN cookie and the HttpOnly attribute is set. As stated initially, I did follow the blog and have implemented the Middleware and configured it in Startup.cs which is why the cookie is set to HttpOnly. The issue is that setting this cookie to HttpOnly results in 400 Bad Requests errors when accessing the Application pages.
-
0
Hi @truist.software,
Could you share your project with support@aspnetzero.com ?
-
0
I cannot share the project but I don't need to. If you just use:
ASP.NET CORE MVC & jQuery: v13.3.0
.NET 8straight from the download and you follow the blog https://aspnetzero.com/blog/http-only-anti-forgery-token-in-asp.net-zero you will see that the XSRF-TOKEN is set to HttpOnly per the blog but the application breaks with 400 Bad Request as you go through the different application features using the menu.
-
0
Hi @truist.software
Your problem of getting 400 error here has been solved in other versions. Here you can use the latest version 14.0.0 if you want. The problem you described does not occur in the latest version.
-
0
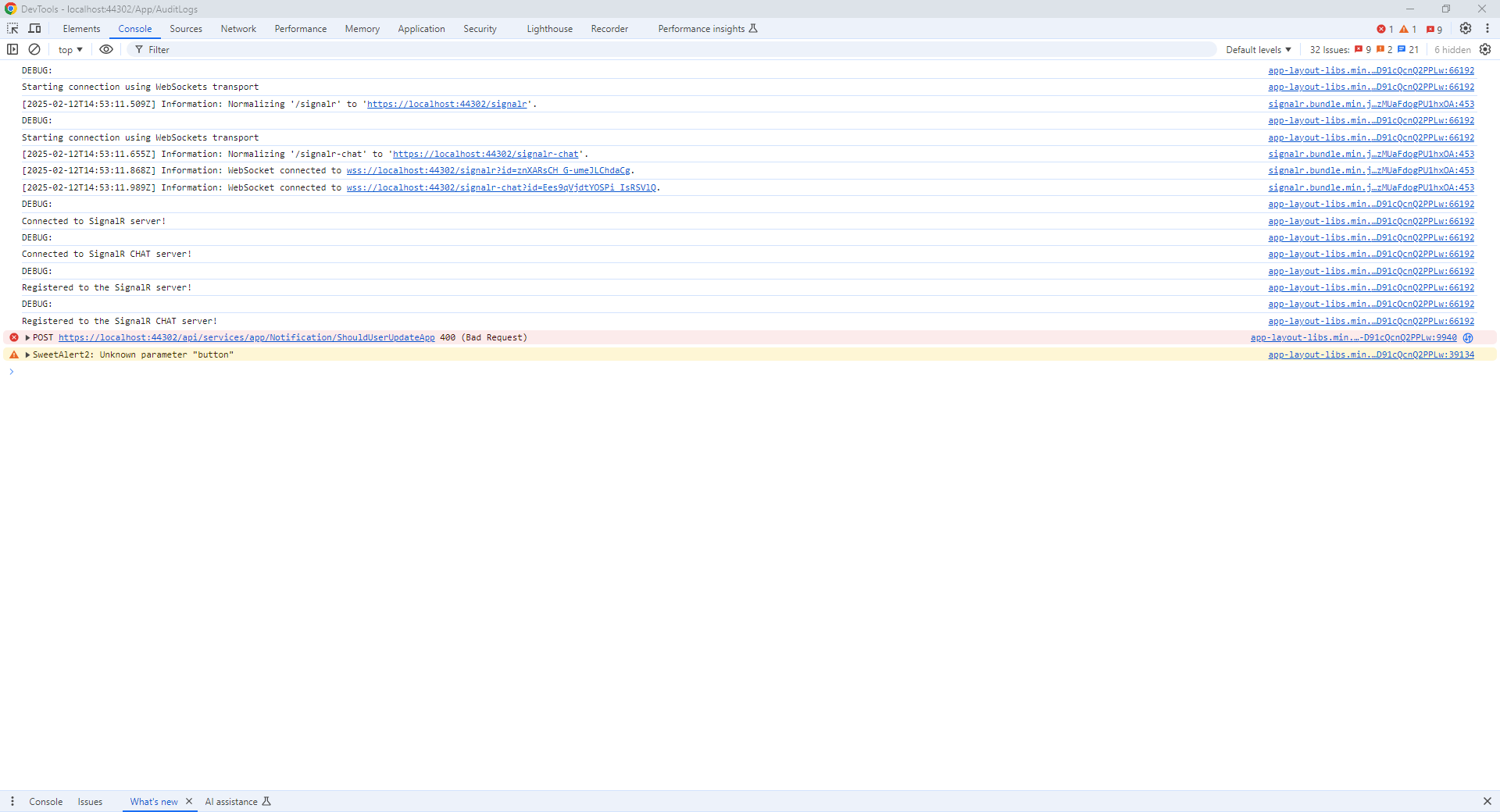
Using the latest version (see below) straight out of the box with no modifications other than implementing "HTTP-Only Anti-Forgery Token in ASP.NET Zero" exactly as presented in the blog. https://aspnetzero.com/blog/http-only-anti-forgery-token-in-asp.net-zero does not solve the issue as you stated above.
The XSRF-TOKEN is set with HttpOnly but the application throws 400 errors. Please advice.
ASP.NET CORE MVC & jQuery: v14.0.0
.NET 9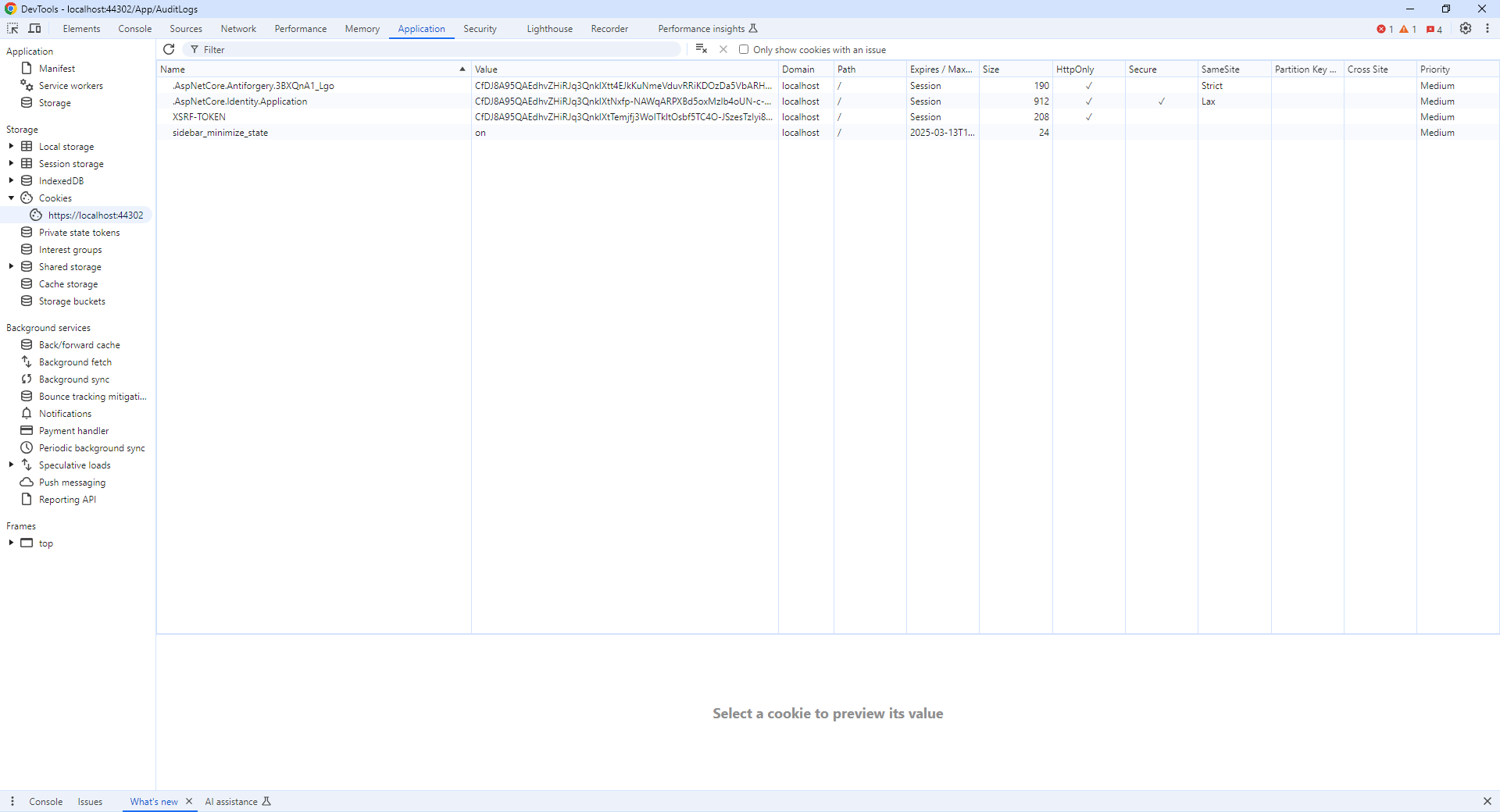
-
0
Hi @truist.software
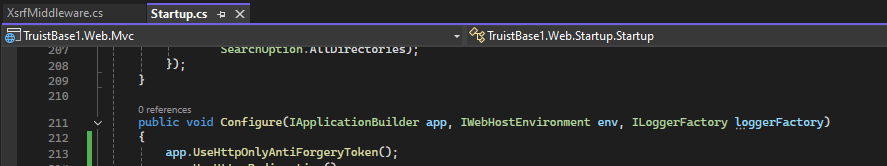
app.UseHttpOnlyAntiForgeryToken();After which ApplicationBuilder extension did you add the add operation? Make sure you add this at the top of theConfiguremethod inStartup.cs.public void Configure(IApplicationBuilder app, IWebHostEnvironment env, ILoggerFactory loggerFactory) { app.UseHttpOnlyAntiForgeryToken(); //Other } -
0
I have it at the top of the Configure method. It still errors out.
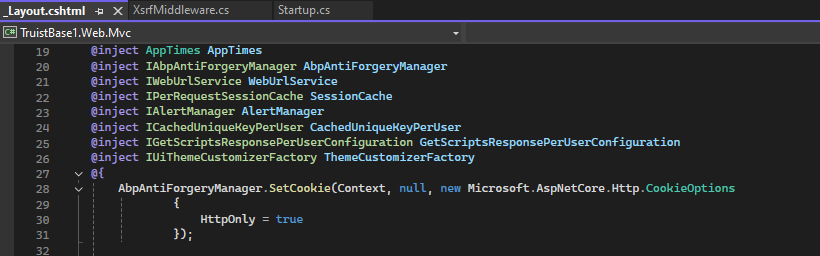
-
0
Hi @truist.software
You need to apply this change in all
SetCookieusage in the project. Have you made this change for allSetCookieusage? -
0
Can you eloborate on "Have you made this change for all SetCookie usage?" I added the SetCookie logic in the _Layout.cshtml per the blog. Does it need to be added to other files/code? If so, where ?
-
0
Hi @truist.software
When you search for
"AbpAntiForgeryManager.SetCookie"in your project, you need to make the changes mentioned in the blog in 8 places. These files are as shown in the screenshot.Before
AbpAntiForgeryManager.SetCookie(Context);After
AbpAntiForgeryManager.SetCookie(Context, null, new CookieOptions { HttpOnly = true });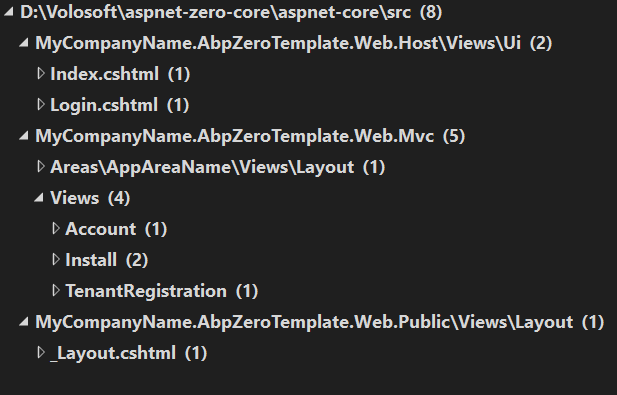
In the *.Web.Host project, you will only need to add the
"HttpOnly = true"setting to Index.cshtml under UI.