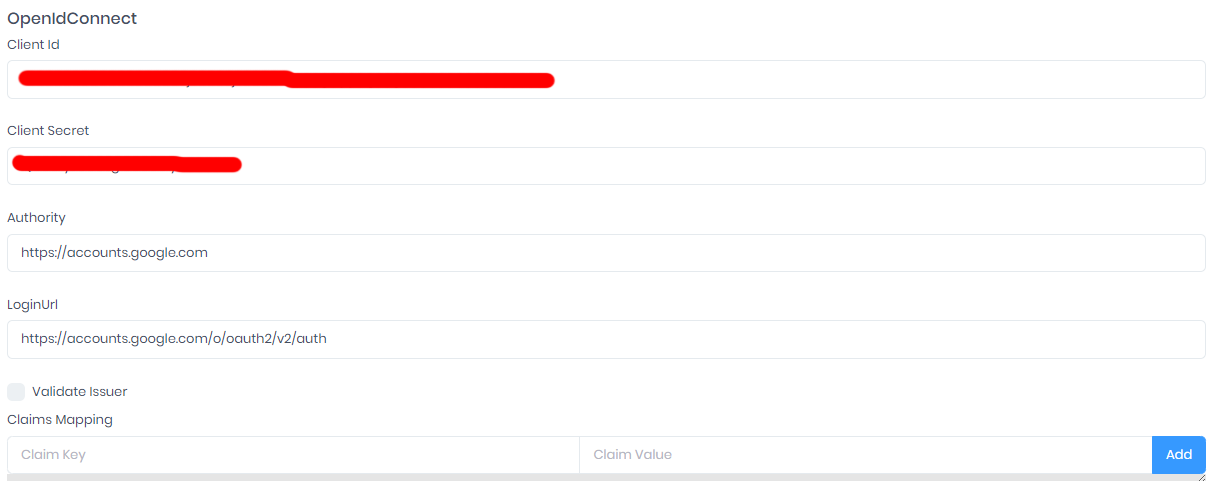
Hello,
we want to provide OpenId SSO capability in our aspnetzero-based solution. We did not modified anything regarding to these parts of the application.
We try to validate it using the Google OpenId API. (We did succeeded to validate the Google External login implementation, so not the OpenId one but the "Google" one in aspnetzero settings).
It fails with a frontend error : "core.js:4197 ERROR Error: Uncaught (in promise): Wrong issuer: https://accounts.google.com"
Here are the settings we used :
Client ID & client secret are definitively OK, they work with "Google" external login settings.
Did we missed something, or the aspnetzero implementation is broken ?
Thanks.
7 Answer(s)
-
0
Hi @Romka
- Is the issuer value exactly same as you configured in your app (Check case sensitivity and ending / character ) ?
- Did you follow a document to configure this ? If so, can you share it ?
Thanks,
-
0
Hi @ismcagdas,
thanks for your reply.
We used the officiel Google documentation here : https://developers.google.com/identity/protocols/oauth2/openid-connect
which states we should use this discovery info to extract issuer / auth urls : https://accounts.google.com/.well-known/openid-configuration
These are the urls we used to configure our application (- "issuer" and "authorization_endpoint" properties in the discovery document), which do match, by the way, the default ones as described in their doc, and all the samples I saw on internet.
I tried with the very same settings on a different PC with the same code branch (but another database) and it throws "System.InvalidOperationException: Sequence contains no matching element" at Abp.AspNetZeroCore.Web.Authentication.External.OpenIdConnect.OpenIdConnectAuthProviderApi.GetUserInfo(String token)
-
0
Hi @Romka
Is your packages below using latest version 2.1.1 ?
Abp.AspNetZeroCore Abp.AspNetZeroCore.WebAlso, can you see the returned token from Google ? Probably one of the claims (name or email) have a different name than AspNet Zero wants it to be.
-
0
Hello,
sorry for this delay, I was on vacation.
It seems you are right, google ODIC does not provide the "email" claim.
The thing I want to achieve is to validate our application does work as OpenId Client. So I can try to make it work using another OIDC server than Google.
Have you got one public site with which it works ? Somethin I can tell my clients "look, OIDC does work in our application, you can check against this provider" ?
Here is what I tried :
- Google : "email" claim not provided
- OIDC Playground (https://openidconnect.net/) : does not work because the redirect url is not configurable
- Github : the login process redirects to http://localhost:4200/login?code=xxxx&state=xxxx, but nothing further, I am not logged in
-
0
Hello, I still need help.
I tried also with Microsoft OpenIdConnect implementation. The aspnetzero "Microsoft" Extenral Login does work. With the same microsoft application, access via OIDC does not work from our application. The returned payload does include name & email claims, I can see it when I decrypt the token. The error is the same than for google : "Sequence contains no matching element", meaning another claim is missing, I suppose.
==> can you please provide us with the right, full, precise list of claims needed for aspnetzero OIDC client to work ? ==> can you improve the documentation ? You can notice than I'm not the only one to face these problems.
I think that Google, Microsoft, Github etc. are not very "exotic" servers, it should work without having to dig into internet 10's of hours, asking support etc.
-
0
Hi @Romka
We thougt about creating a document about this but every auth provider has its own wya for configruation. Here are the list of claims AspNet Zero requires;
- aud (audiance claim)
- name (full name of the user or can just be the name)
- unique_name (email addres claim)
If your provider returns a different name for one of those claims, you can map them as I shared before. If you also upgrade packages below in your solution, you can see a proper error message about the missing claims.
- Abp.AspNetZeroCore
- Abp.AspNetZeroCore.Web
Could you share the token returned from yoru auth provider via email with [email protected] if you can't solve this problem ?
-
0
Ok,
So I managed to get it work by adding a claim mapping between preferred_username (sent by microsoftonline) and unique_name (needed by aspnetzero).
So it works, thanks.