Activities of "echonos"
Hi @ismcagdas
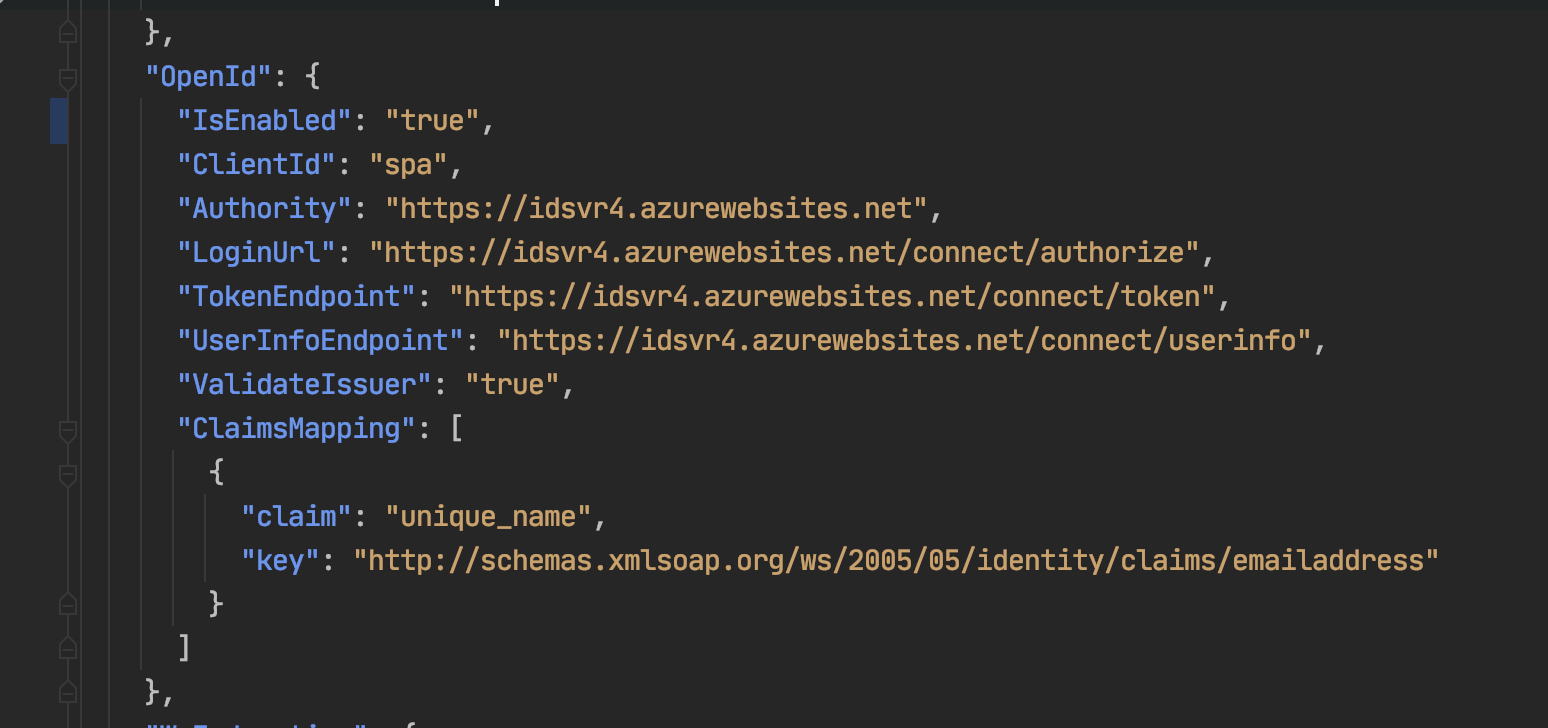
We do not need the "abp.tenantid" header for the request made to the OpenId provider. This request is not made to abp.zero backend Api, it's made to OpenId provider token endpoint by angular-oauth2-oidc library.
Yes, after a troubleshooting session, our customer says the request is work correctly if removing this header
- What is your product version? v9.3.0
- What is your product type (Angular or MVC)? Angular
- What is product framework type (.net framework or .net core)? .net core
We are trying to make external login with open id connect. Our client uses PingFederate (PingIdentity) for the identity server. We are using the open id login process with Auth Code Flow + PKCE.
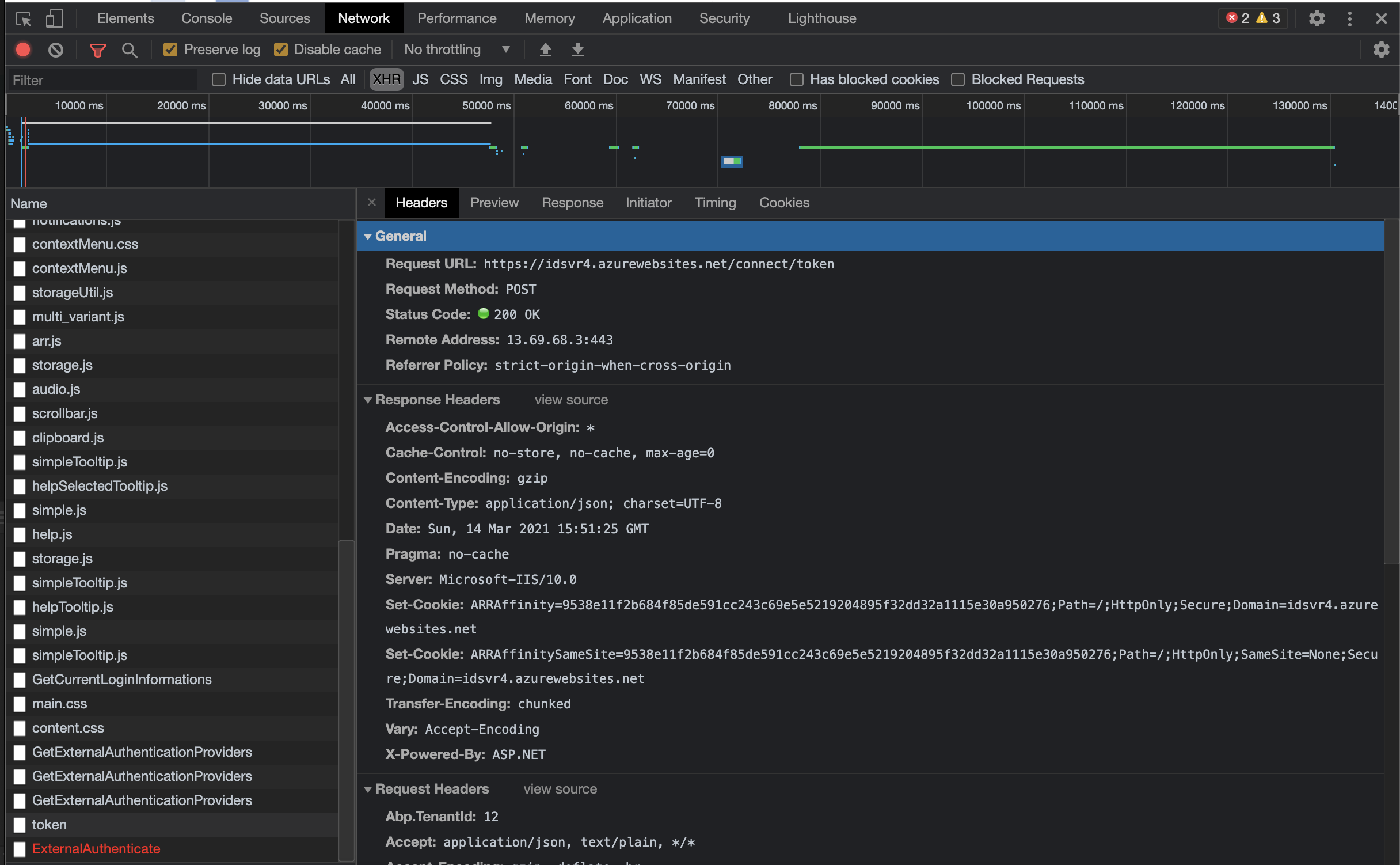
The user is logged in from the authorization endpoint and successfully redirects to our application. Then the request sent to the token endpoint gets stuck with a cors error. Actually, by default, our client grants cors permissions for the token endpoint, but we get a cors error due to the extra headers such as "abp.tenantid" in the request sent. How can I remove the "abp.tenantid" header from this request? what can you suggest to remove this header?
Thank you!
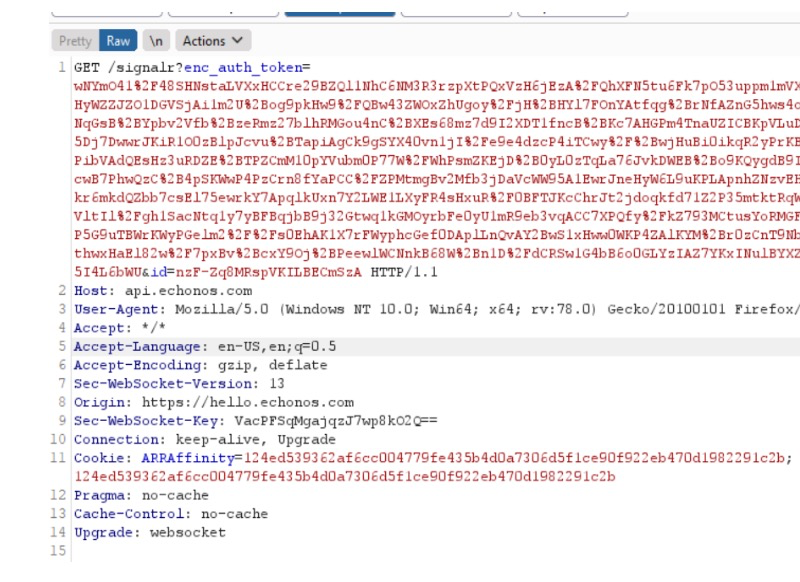
GET /signalr?enc_auth_token=token
<br> We just recently had our .net zero based application audited by a security company. We were told that SignalR GET request includes the authentication token as querystring parameter, which happens to pose a high security risk. We were recommended to use the POST method but we could not find the right place to implement this solution. What would you recommend as a solution?