Activities of "hra"
We have been a customer since 2020, and have just recently started our upgrade to v13 in November - but have been paying for license all the way in between. I am concerned about some issues that may indicate that this product is not receiving the maintenance attention that it should.
- Microsoft ADAL was completely broken in v13 - the ADAL library was not being 'initialized()' at all - somehow this crept through QA. github
- PrimeNG treeview checkboxes could not be "ticked" at all - somehow this crept through QA github
- There are other libraries that the code references that are no longer supported and shouldn't be in the product msal
- I cannot successfully run "npm install" in the default (unmodified) angular project template at all - it complains about incompatible implicit dependencies on out-of-date angular-core versions. Some of these track back to 3rd party libraries that are long out of support (@craftjs/perfect-scrollbars") - last updated 6 years ago.
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.0" from primeng@17.18.12
npm warn node_modules/primeng
npm warn primeng@"^17.18.9" from the root project
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@0.15.0
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm warn ERESOLVE overriding peer dependency
npm warn While resolving: @angular/core@18.2.13
npm warn Found: zone.js@undefined
npm warn node_modules/zone.js
npm warn zone.js@"~0.15.0" from the root project
npm warn
npm warn Could not resolve dependency:
npm warn peer zone.js@"~0.14.10" from @angular/core@18.2.13
npm warn node_modules/@angular/core
npm warn @angular/core@"^18.2.3" from the root project
npm warn 24 more (abp-ng2-module, angular-gridster2, ...)
npm error code ERESOLVE
npm error ERESOLVE could not resolve
npm error
npm error While resolving: @craftsjs/perfect-scrollbar@5.1.0
npm error Found: @angular/core@18.2.13
npm error node_modules/@angular/core
npm error @angular/core@"^18.2.3" from the root project
npm error peer @angular/core@"^18.1.1" from abp-ng2-module@11.0.0
npm error node_modules/abp-ng2-module
npm error abp-ng2-module@"^11.0.0" from the root project
npm error 23 more (angular-gridster2, angular-oauth2-oidc, ...)
npm error
npm error Could not resolve dependency:
npm error peer @angular/core@">=15.0.0 < 16.0.0" from @craftsjs/perfect-scrollbar@5.1.0
npm error node_modules/@craftsjs/perfect-scrollbar
npm error @craftsjs/perfect-scrollbar@"^5.1.0" from the root project
npm error
npm error Conflicting peer dependency: @angular/core@15.2.10
npm error node_modules/@angular/core
npm error peer @angular/core@">=15.0.0 < 16.0.0" from @craftsjs/perfect-scrollbar@5.1.0
npm error node_modules/@craftsjs/perfect-scrollbar
npm error @craftsjs/perfect-scrollbar@"^5.1.0" from the root project
npm error
npm error Fix the upstream dependency conflict, or retry
npm error this command with --force or --legacy-peer-deps
npm error to accept an incorrect (and potentially broken) dependency resolution.
I am regenerating my client proxies from our AspNetZero swagger document (v14). I am getting conflicts, the proxy generator is creating classes from the swagger contract that conflict with names in Dart (its a flutter app). Looking into this, the swagger document contains definitions for MethodInfo, Type, Assembly, etc etc - the BCL runtime classes from .NET. This seems like a massive over-step. I've checked the AspNetZero demo site, and it also returns all these CLR classes int he swagger document - surely that shouldn't be necessary?? It seems very dirty, and obviously a possible cause of issues. Do these need to be in here, and if not, what's pulling them in, and how do we get rid of them?
Thanks.
Hi Team,
We're working through updating our aspnet zero project
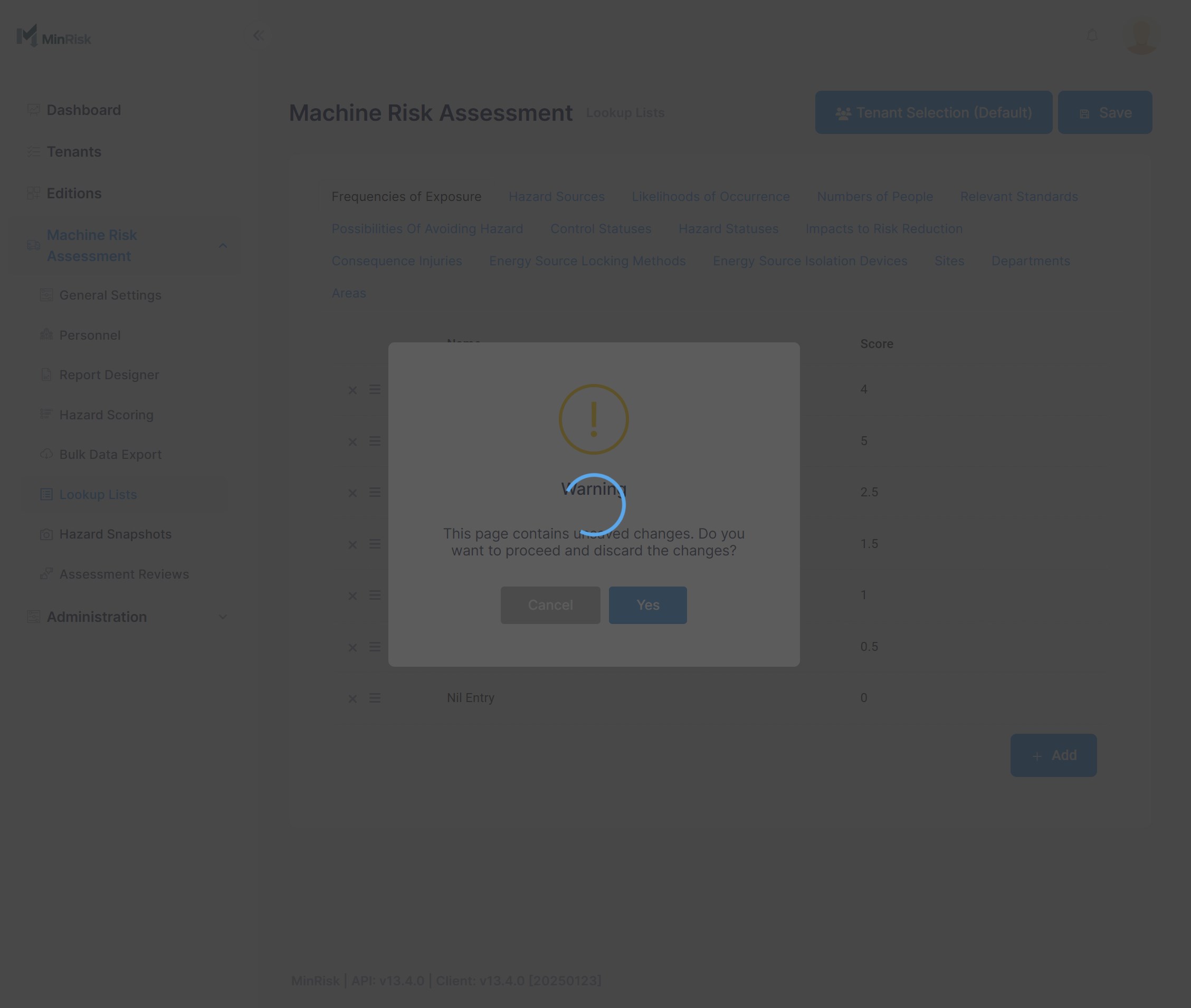
We've noticed that the alert box that is supposed to show when navigating away from page with unsaved changes shows underneath the loading spinner (see screenshot below)
Our code looks like this:
import { CanDeactivate, ActivatedRouteSnapshot, RouterStateSnapshot, UrlTree } from "@angular/router";
import { Injectable } from '@angular/core';
import { Observable, Subject } from "rxjs";
import { MessageService, LocalizationService } from "abp-ng2-module";
import { AppConsts } from "../../AppConsts";
@Injectable()
export class CanDeactivateUnsaved implements CanDeactivate<ICanSaveChanges> {
localizationSourceName = AppConsts.localization.defaultLocalizationSourceName;
constructor(
private localization: LocalizationService,
private _message: MessageService
) { }
canDeactivate(
component: ICanSaveChanges,
currentRoute: ActivatedRouteSnapshot,
currentState: RouterStateSnapshot,
nextState: RouterStateSnapshot
): Observable<boolean | UrlTree> | Promise<boolean | UrlTree> | boolean | UrlTree {
if (component.hasChanges) {
return new Promise<boolean>((resolve, reject) => {
this._message.confirm(
this.l('UnsavedChanges'),
this.l('Warning'),
isConfirmed => {
resolve(isConfirmed);
//if (isConfirmed)
// component.Save();
}
);
});
}
return true;
}
}
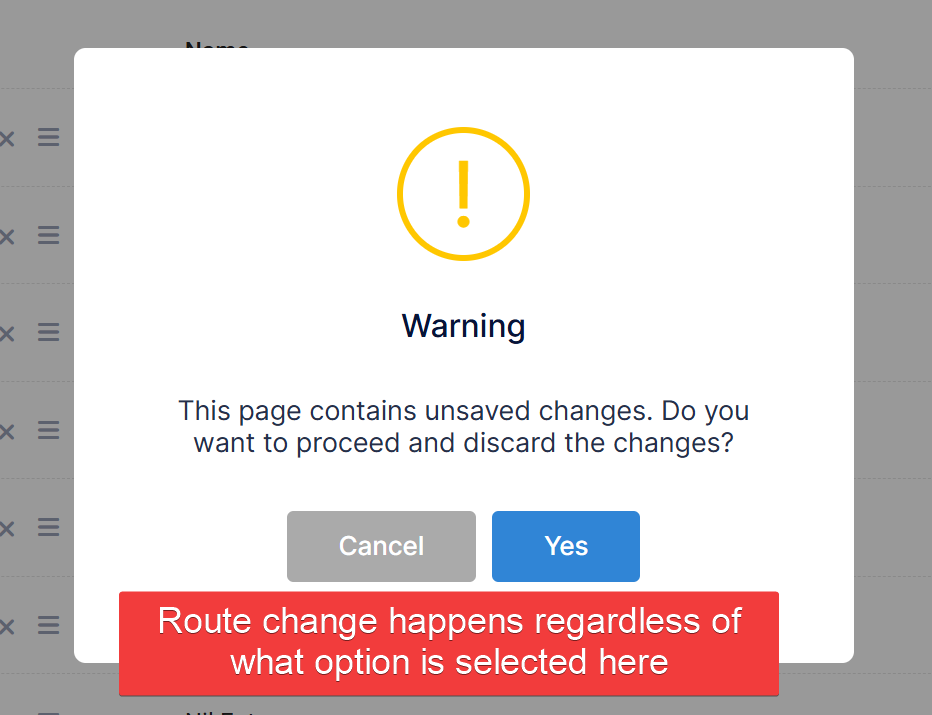
The route change happens regardless of whether "cancel" or "save" is selected in the confirmation modal:
Hi @hra
Thanks. Is it possible for you to create an issue on https://github.com/aspnetzero/aspnet-zero-core ? We can re-evaluate this.
Thanks, done: https://github.com/aspnetzero/aspnet-zero-core/issues/5084
Thanks @ismcagdas,
Just to be clear - please note that I changed my example to return a POCO instead of IActionResult - just to prove it actually makes no difference what the return type is - the problem remains.
Thanks for helping out here. What I am concerned about, is that while I've been building our product on ANZ, I have inadvertently caused the authentication behavior to deviate between ControllerBase and ApplicationServer. If you find that baseline ANZ correctly returns HTTP 402 for both ControllerBase and ApplicationService, then I'm going to need to figure out how I've broken it. If, however, you find that ControllerBase fails to return the same HTTP error code as an ApplicationService, when you have an invalid token - then I guess we can work together to fix both our code bases.
Of course, I'm quietly rooting for the latter :)
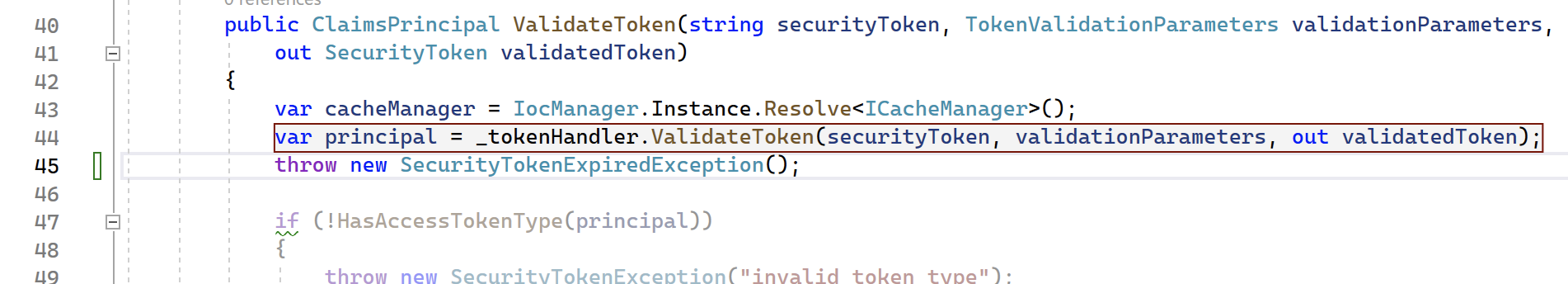
Note: A real easy way to test this without mucking around with tokens, is in ProductJwtSecurityTokenHandler.cs on line 45, simply throw exception.
Hi - thanks for the quick response,
Please note that my "hack" was just one way to reproduce this behavior. It could have just as easily occurred by a user account becoming unavailable (deletion?) during token refresh - or possibly there is another way for the user to not be found - the original author of TokenAuthController appears to have thought so when they wrote it.
Here's my thinking...
- whomever wrote TokenAuthController.Refresh was clearly intending to handle the case where a user could not be found for the user-id claim - because they are testing for "user == null"
- when "user == null" they are throwing a UserFriendlyException - which is great - it provides some insight to the end user - instead of just HTTP500.
- unfortunately, the code checking for null being returned from GetUserAsync will never evaluate to true - because GetUserAsync cannot return null (it throws an exception internally if null is detected).
- the ACTUAL result of a user not being found, is GetUserAsync throws an Exception, which is caught by the Refresh method catch-all handler, which then rethrows as a ValidationException, which then gets mapped to HTTP500 - a very unhelpful error.
Hopefully I've described my thinking clearly - I agree with the original intent of the code, to deliver useful information about the user not being found, to the end user - however the way it's implemented prevents that intent from being realised - with code that can never be reached by the instruction pointer...
Thanks @ismcagdas
Hi,
Does it make any difference if you use
AbpAuthorizeinstead ofAbpMvcAuthorize?
No difference. Incidentally, I did originally use AbpAuthorize, I only recently switched it to AbpMvcAuthorize while I was trying to overcome this issue.
What is your answer to
- I am expecting that an expired token should trigger the same HTTP result code (401) if the client is calling a ControllerBase method, or an ApplicationService method. Currently that is not the case. Should I be expecting that?
I am testing authentication failure to ensure our smart client (a mobile application) is resilient.
During this testing, I will obtain an authentication token from one environment, and then use that token against another environment (yes, a crazy use-case, but this is just a byproduct of trying to debug a collateral issue).
The token is successfully decoded by the different environment, however, the user id does not exist on that environment, so it throws an exception with the relevant information. I found that, instead of returning useful information, such as "invalid refresh token", the server just returns an unhelpful HTTP 500.
I dug a little deeper, an I found that any time the server receives an invalid token, it will 500 instead of giving an appropriate response.
The reason for this is:
https://github.com/aspnetzero/aspnet-zero-core/blob/c3941a4248476419e91071448956468e7e985f16/aspnet-core/src/MyCompanyName.AbpZeroTemplate.Web.Core/Controllers/TokenAuthController.cs#L249 When an invalid token is received, either because the token payload is invalid (line 256) or because the user id within the payload is not found (264) the method throws an ValidationError. (note: line 268 checks user for null, but this code never executes because UserManager.GetUserAsync explicitly throws an Exception when no user is found - hence line 268 is redundant (this in itself is a bug)
The AbpExceptionFilter then wraps this exception, and because the type "ValidationException" does not match any of the mappable types in the abp DefaultErrorInfoConverter, the error is simply mapped to HTTP 500.
So, there are 2 bugs here.
The following line is redundant because GetUserAsync cannot return null: https://github.com/aspnetzero/aspnet-zero-core/blob/c3941a4248476419e91071448956468e7e985f16/aspnet-core/src/MyCompanyName.AbpZeroTemplate.Web.Core/Controllers/TokenAuthController.cs#L268
And "ValidationException" is probably the wrong exception to throw - I think it should be something like AbpAuthorizationException - allowing the client to explain to the user, or at least figure out that token refresh is not going to work, and tell the user that they need to provide their credentials again - as opposed to retrying the same operation.
Of course, I dont know how this change will affect the rest of the application - so it would need to be assessed.
Hi @ismcagdas,
The authorization filter never fires if I'm calling a ControllerBase method with an expired token - neither my customised one you recommended, nor the built-in ABP one - which is not surprising, because this specifically relates to an expired token that is being passed - so the MS auth middleware would be rejecting the request pretty early.
Calling an ApplicationService function with an expired token DOES execute the authorization filter however.
So, clearly the logic of the Authorization Filter is not the cause, because it never gets a chance to run.
When I disable the below code - the auth filter does fire, and I get the correct result back - but I already knew that. The "UseStatusCodePages" middleware appears to be the cause - but I didnt add that - it's part of ANZ.
app.UseStatusCodePagesWithRedirects("~/Error?statusCode={0}");
So, a couple of core questions
- I am expecting that an expired token should trigger the same HTTP result code (401) if the client is calling a ControllerBase method, or an ApplicationService method. Currently that is not the case. Should I be expecting that?
- Assuming it IS a bug - where to from here. Clearly, the authorizationfilter log is good, because when it runs I get the correct result, when it never fires I get a bad result.
Thanks!
Hi, I get a failure with this example
namespace HRA.Portal.Web.Controllers
{
[AbpMvcAuthorize]
[Route("Sync/[action]")]
[DisableAuditing]
public class SyncController : PortalControllerBase
{
public SyncController()
{
}
[HttpPost]
public Task<MyResult> UploadFile()
{
return Task.FromResult(new MyResult());
}
}
public class MyResult
{
}
}