Activities of "ivanosw1"
Ok, I got it.
Thank you very much.
Thank you @ismcagdas
And what happens if you choose two different sopendid servers (google and twitter) but only want one account on the ANZ?
I mean that if I have a Twitter (myuser@twitter.com) and a Google (myuser@google.com) account and the first time I choose Twitter for authentication, and the second time I choose Google, ANZ will create two differents accounts?
Ok, this configuration is correct. The email is mapped. Thank you very much.
Just one question about this: I noticed that the username is a hash value. Is it by design to deny direct access to ANZ with this account created by openid? And what happens if you choose two different sopendid servers (google and twitter) but only want one account on the ANZ?
- What is your product version? 11.2
- What is your product type (Angular or MVC)? Angular
- What is product framework type (.net framework or .net core)? .net core
If issue related with ABP Framework
- What is ABP Framework version? 7.2.1
I've read many post about but I think the problem of email mapping is still alive. AspnetZero configured to use Abp.Io as Oaut2 server.
Abp.Io configuration says that email is returned (and is true)
{
"issuer": "https://localhost:44322",
"jwks_uri": "https://localhost:44322/.well-known/openid-configuration/jwks",
"authorization_endpoint": "https://localhost:44322/connect/authorize",
"token_endpoint": "https://localhost:44322/connect/token",
"userinfo_endpoint": "https://localhost:44322/connect/userinfo",
"end_session_endpoint": "https://localhost:44322/connect/endsession",
"check_session_iframe": "https://localhost:44322/connect/checksession",
"revocation_endpoint": "https://localhost:44322/connect/revocation",
"introspection_endpoint": "https://localhost:44322/connect/introspect",
"device_authorization_endpoint": "https://localhost:44322/connect/deviceauthorization",
"frontchannel_logout_supported": true,
"frontchannel_logout_session_supported": true,
"backchannel_logout_supported": true,
"backchannel_logout_session_supported": true,
"scopes_supported": ["openid", "profile", "email", "address", "phone", "role", "AccountService", "IdentityService", "AdministrationService", "SaasService", "ProductService", "offline_access"],
"claims_supported": ["sub", "birthdate", "family_name", "gender", "given_name", "locale", "middle_name", "name", "nickname", "picture", "preferred_username", "profile", "updated_at", "website", "zoneinfo", "email", "email_verified", "address", "phone_number", "phone_number_verified", "role"],
"grant_types_supported": ["authorization_code", "client_credentials", "refresh_token", "implicit", "password", "urn:ietf:params:oauth:grant-type:device_code", "LinkLogin", "Impersonation"],
"response_types_supported": ["code", "token", "id_token", "id_token token", "code id_token", "code token", "code id_token token"],
"response_modes_supported": ["form_post", "query", "fragment"],
"token_endpoint_auth_methods_supported": ["client_secret_basic", "client_secret_post"],
"id_token_signing_alg_values_supported": ["RS256"],
"subject_types_supported": ["public"],
"code_challenge_methods_supported": ["plain", "S256"],
"request_parameter_supported": true
}
The email address is returned after a succesfull login

The email is not mapped in database
Open id configuration:
"OpenId": {
"IsEnabled": "true",
"ClientId": "UnoIns",
"Authority": "https://localhost:44322",
"LoginUrl": "https://localhost:44322/connect/authorize",
"ValidateIssuer": "false",
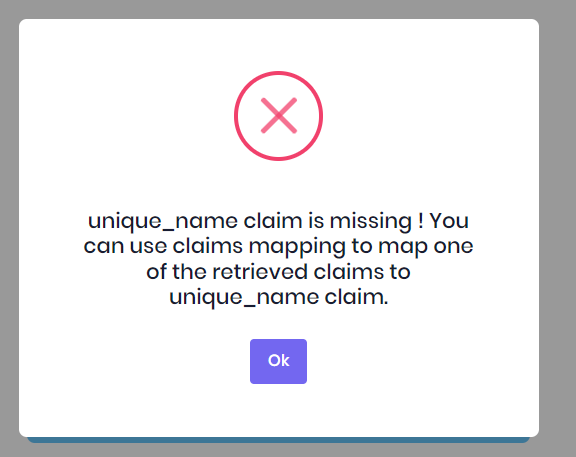
"ClaimsMapping": [
{
"claim": "name",
"key": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name"
},
{
"claim": "email",
"key": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress"
},
{
"claim": "unique_name",
"key": "preferred_username"
}
]
},
Angular configuration:
private getOpenIdConnectConfig(loginProvider: ExternalLoginProvider): AuthConfig {
let authConfig = new AuthConfig();
authConfig.loginUrl = loginProvider.additionalParams['LoginUrl'];
authConfig.issuer = loginProvider.additionalParams['Authority'];
authConfig.skipIssuerCheck = loginProvider.additionalParams['ValidateIssuer'] === 'false';
authConfig.clientId = loginProvider.clientId;
authConfig.responseType = 'id_token';
authConfig.redirectUri = window.location.origin + '/account/login';
authConfig.scope = 'openid profile email';
authConfig.requestAccessToken = false;
return authConfig;
}
What I'm missing?
Thank you.
Hi, I've the same need: populate targerUrl field in a UserFriendlyException. There is a way to achieve that?
Thank you
Abp 9.3.0 Core + Angular
Hi @andmattia, our solution is more simple and less invasive. Abp still keeps it's own authentication system. We have enable identity server only for authenticate "service/not human" clients and created a custom authorization attribute to protect route using scopes.
Any news about this topic?
Hi, I need to register users with a space (one o more) in the user name. This is a constraint and cannot be changed because the login auth is external to Abp. Where can I configure Abp to achive this requirement? This is the error: (Abp.UI.UserFriendlyException: User name 'DE ROSSI01' is invalid, can only contain letters or digits.
Thank you.
- What is your product version? 9.3.0
- What is your product type (Angular or MVC)? Angular
- What is product framework type (.net framework or .net core)? Core
Hi @elferone
At the end we have separated Abp authentication from Identity Server. Each services talk directly to Identiy Server with client credential authentication to obtain a token. The service's endpoints are protected by a custom attribute that validate the token issued by identity server (scope, validity, issuer, end so on).