Activities of "maliming"
hi
But when I am using the base code and add that https redirect code in auth configure it works, but not with the custom code in MyOpenIdChallengeResult.cs why is it so?
I don't understand what you mean.
What is your current code for MyOpenIdChallengeResult?
What do you mean not work?
Also right now internally on nginx our application runs on http will the fix shared by you will disturb this setting?
No.
hi
FYI - our application is running on linux server over nginx
You can add a middleware code.
https://github.com/maliming/CDP-Base-Zero-13.0.0/commit/5152c06f8459c96cbd2b416f02fc910a22a80843
app.Use((ctx, next) =>
{
ctx.Request.Scheme = "https";
return next();
});
hi
Please also share a username and password of https://fynauth0.uk.auth0.com/
You can create a new account of liming.ma@volosoft.com
hi
Can you add code to reproduce the problem in https://github.com/maliming/CDP-Base-Zero-13.0.0
hi
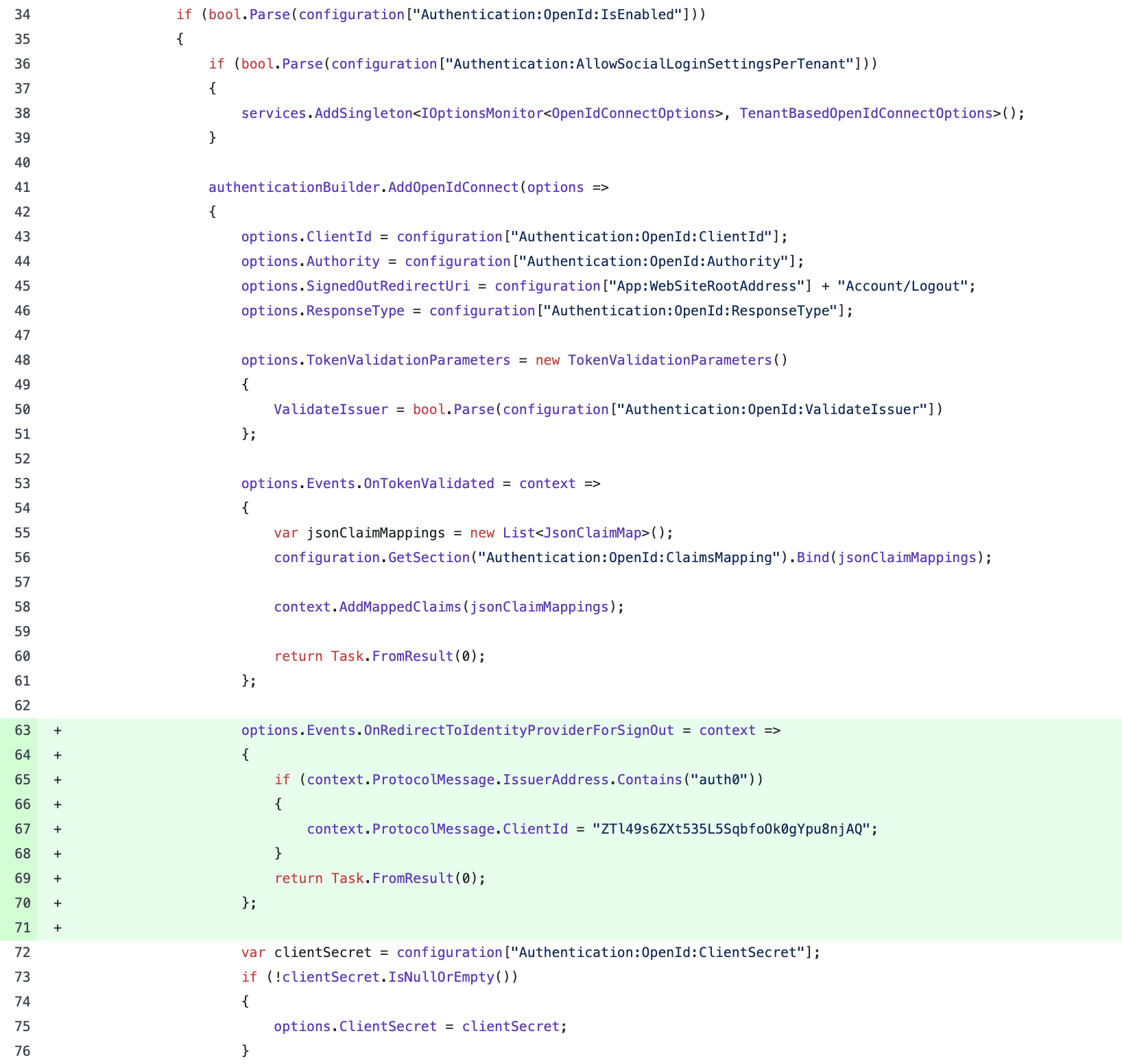
Auth0 says if you pass the client id while logout then you can setup at application level, but if you don't pass client id you will require to set at tenant level
You can add your client id during logout.
options.Events.OnRedirectToIdentityProviderForSignOut = context =>
{
if (context.ProtocolMessage.IssuerAddress.Contains("auth0"))
{
context.ProtocolMessage.ClientId = "ZTl49s6ZXt535L5SqbfoOk0gYpu8njAQ";
}
return Task.FromResult(0);
};
hi
why I need to add at the tenant level. Why its not working by just adding at the application level.
This is an auth0 problem, I have no ideas.
hi
You can add a new property to ExternalAuthenticateModel class to indicate the auth0 or okta.
hi
The issue I am facing is I am getting external.Succeeded value as false.
Can you share your project code?
Or upload it to GitHub, then invite me to check?
https://github.com/maliming