Activities of "mdepouw"
Is there a way to configure multiple OpenID Connect providers out the box?
reference: Authentication configuration:
{
"Authentication": {
"AllowSocialLoginSettingsPerTenant": false,
"Facebook": {
"IsEnabled": "false",
"AppId": "",
"AppSecret": ""
},
"Twitter": {
"IsEnabled": "false",
"ApiKey": "",
"ApiKeySecret": ""
},
"Google": {
"IsEnabled": "false",
"ClientId": "",
"ClientSecret": "",
"UserInfoEndpoint": "https://www.googleapis.com/oauth2/v2/userinfo"
},
"Microsoft": {
"IsEnabled": "false",
"ConsumerKey": "",
"ConsumerSecret": ""
},
"OpenId": {
"IsEnabled": "true",
"ClientId": "4fb5e652-dc58-4370-95ca-fdfb3ba46273",
"Authority": "https://spottedmahnb2c.b2clogin.com/spottedmahnb2c.onmicrosoft.com/B2C_1_BlahNewFormat/v2.0/",
"Issuer": "https://spottedmahnb2c.b2clogin.com/80033dfd-6eab-42c4-bdf2-4e223d4b396f/v2.0/",
"LoginUrl": "https://spottedmahnb2c.b2clogin.com/spottedmahnb2c.onmicrosoft.com/B2C_1_BlahNewFormat/oauth2/v2.0/authorize",
"ValidateIssuer": "true",
"ResponseType": "id_token",
"ClaimsMapping": [{
"claim": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier",
"key": "name"
}, {
"claim": "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress",
"key": "emails"
}
]
},
"WsFederation": {
"IsEnabled": "false",
"Authority": "",
"ClientId": "",
"Tenant": "",
"MetaDataAddress": ""
},
"JwtBearer": {
"IsEnabled": "true",
"SecurityKey": "DemoProjectDemo_blah",
"Issuer": "DemoProjectDemo",
"Audience": "DemoProjectDemo"
}
}
}
I'm confused as to why we don't have access to the source code for Abp.AspNetZeroCore.Web. Shouldn't that source be available in one of the private repo's in https://github.com/aspnetzero? If we have an active license don't we have access to the source code?
What am I misunderstanding?
reference other posts about this topic:
https://support.aspnetzero.com/QA/Questions/4571#answer-86b1a766-de44-49d6-aa29-fa0f014f9e5d
yeah this package is closed source due to licensing purposes.
and https://support.aspnetzero.com/QA/Questions/8511/Access-to-the-AbpAspNetZeroCoreWeb
Hi @ismcagdas - any updates? Are my customizations required or am I doing something wrong? thanks!
Hi @ismcagdas 👋 - unfortunately no. We need multiple OpenID connect providers within one tenant.
sidenote: question title updated to better reflect the ask
Hi @ismcagdas 👋
- The solution also has a closed-source NuGet package that is used to protect ASP.NET Zero's license rules. source
That part makes sense 👍. If the source was available for license checking then one could subvert the rules & modify that code. But, anything outside of that, why make that closed source? 🤔
For example, I'm extending ASP.NET Zero to support multiple OpenID providers in one tenant & I wanted to understand how Abp.AspNetZeroCore.Web.Authentication.External.ExternalAuthManager is behaving.
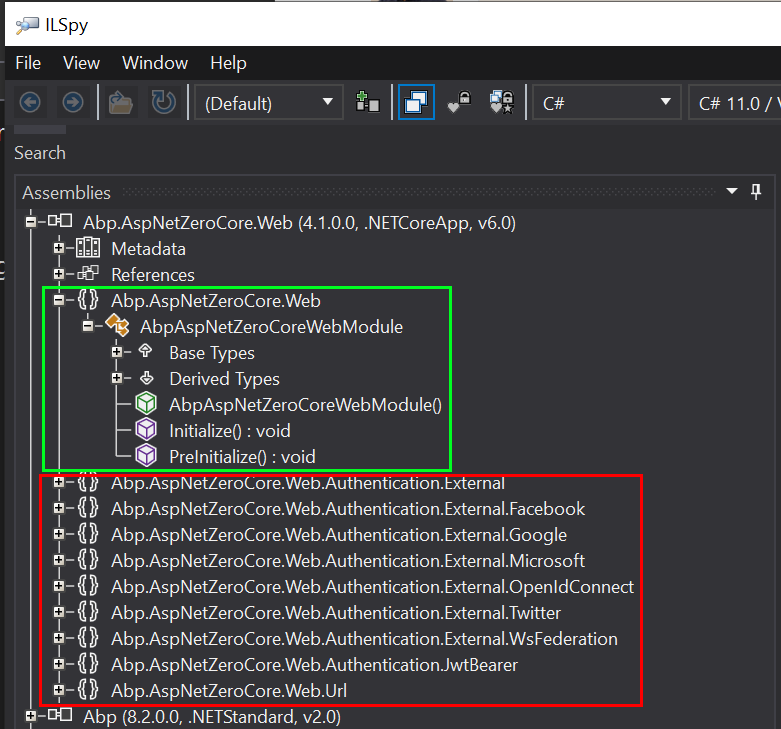
Please see the screenshot below... the green I get & is properly related to licensing but the red, how does that related to licensing? 🤔
Not a huge deal, just trying to understand 😊, thanks!
Currently this is not supported
I figured that was the case. I didn't want to start customizing when there's some functionality I wasn't aware of. GTG, thanks!
So, you may create a new OIDC provider with OpenIdConnect2 for example to support second OIDC provider.
That's the path I was heading down 😊! The issue I came across when doing that was on ExternalAuthManager.GetUserInfo(). The provider is not passed through to OpenIdConnectAuthProviderApi.GetUserInfo().
In the returned object, I can see the Provider is hardcoded 😢. I ended up overriding the Provider after calling the method. i.e.
var userInfo = await _externalAuthManager.GetUserInfo(model.AuthProvider, model.ProviderAccessCode);
// ugly!
userInfo.Provider = model.AuthProvider;
return userInfo;
Decompiled code snippet of OpenIdConnectAuthProviderApi:
public class OpenIdConnectAuthProviderApi : ExternalAuthProviderApiBase
{
public override async Task<ExternalAuthUserInfo> GetUserInfo(string token)
{
...
return new ExternalAuthUserInfo
{
Provider = "OpenIdConnect",
ProviderKey = validatedTokenResult.Token.Subject,
Name = fullNameParts[0],
Surname = ((fullNameParts.Length > 1) ? fullNameParts[1] : fullNameParts[0]),
EmailAddress = emailClaim.Value,
Claims = validatedTokenResult.Principal.Claims.Select((Claim c) => new ClaimKeyValue(c.Type, c.Value)).ToList()
};
}
}
Please see the screenshot below... the green I get & is properly related to licensing but the red, how does that related to licensing? 🤔
My question still stands though 😊
Next challenge, how can I add additional configuration fields to an OpenID Connect provider if that source code is not modifiable?
I wanted to add Issuer and WellKnown to appsettings.json for supporting Azure AD B2C but I'm not seeing a way w/o hacking up the code. Seems like a pretty simple thing, add a few more fields to the config & modify the code that's reading it but that's not the case here.
I'm not seeing it, what does "license control code" have to do w/ external authentication? 🤔
You can inject IConfigurationRoot to read appsetting.json
That was not giving me the full config. But, I injected IWebHostEnvironment env and then called env.GetAppConfiguration() which gave me a IConfigurationRoot that did have all the config.