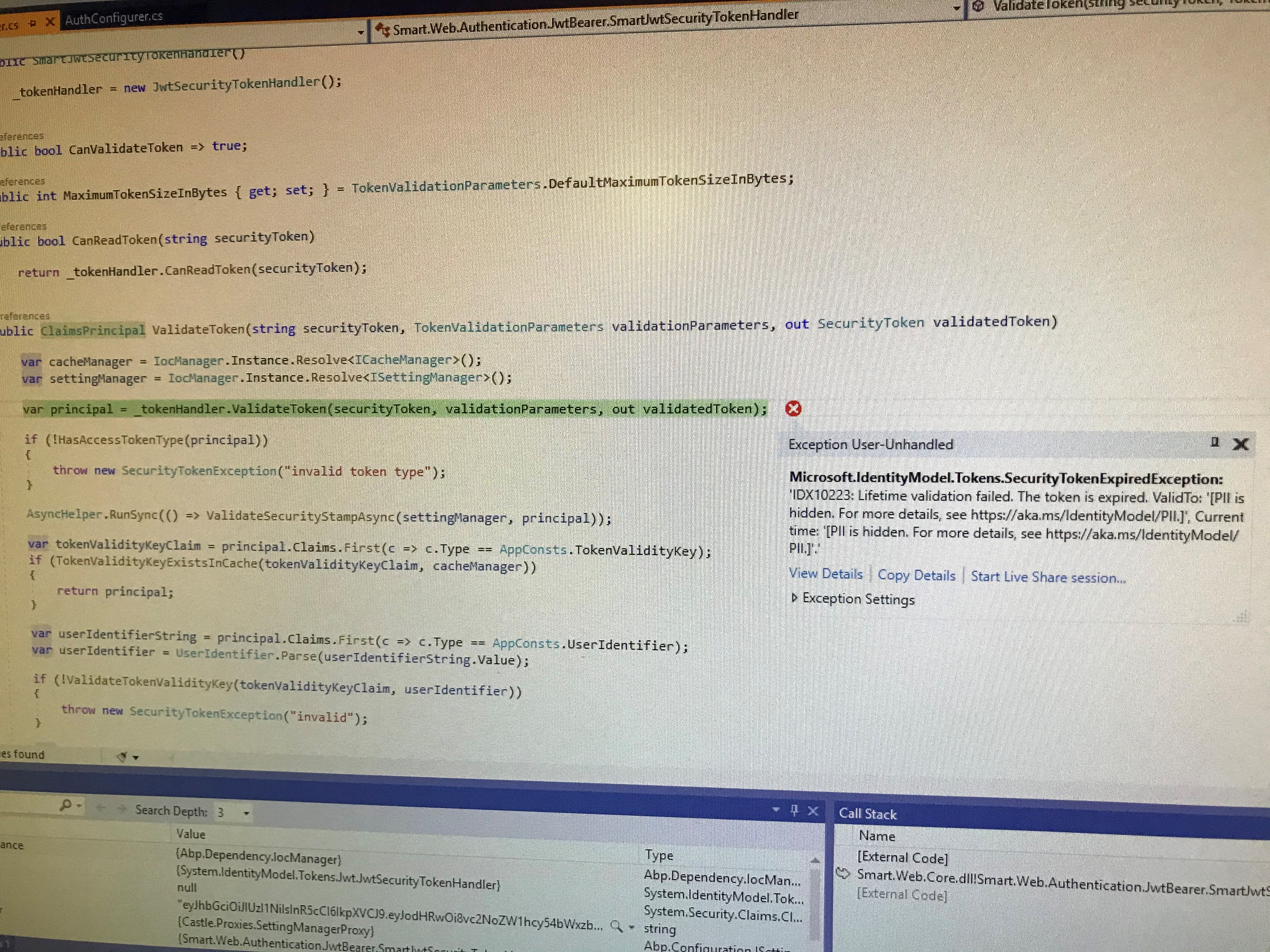
Hi
App in dev mode keeps failing with the following thrown exception:
IDX10223: Lifetime validation failed. The token is expired. ValidTo: '[PII is hidden]', Current time: '[PII is hidden]'.
46 Answer(s)
-
0
Can you please check if your AccessTokenExpiration has so small time? Its located in
*.Application.Shared-> AppConsts.cs -
0
Thanks for your feedback.
I have the following values:
public static TimeSpan AccessTokenExpiration = TimeSpan.FromDays(1); public static TimeSpan RefreshTokenExpiration = TimeSpan.FromDays(365);I'm getting this (in dev) multiple times a day. Fixing this requires closing browser and restarting app.
Note: I've been struggling a crash on production without any logs. Do you think this can be related?
-
0
What is your abp version? What is your zero version? It is angular project or mvc?
And additionally, can you please share an error screenshot with more detail?
-
0
AspNetCore + Angular v7.2.3
-
0
@kasem
Can you please share an error screenshot & error stack with more detail?
-
0
Hi!
Sorry for the late reply. Attaching the requested
It turns out that this a very serious problem as it's related to many tickets I created here that haven't been closed yet. It wasn't clear that this problem is serious to that extent. The side-effect of this problem is seriously impacting my production app due to many related crashes happening everyday. I've recently discovered that crashes in production are happening with users leaving app idle for sometime (~30min) exactly as it happens to me in development mode. Appreciate your support to help fixing this urgently.
Stack trace: at Microsoft.IdentityModel.Tokens.Validators.ValidateLifetime(Nullable
1 notBefore, Nullable1 expires, SecurityToken securityToken, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateLifetime(Nullable1 notBefore, Nullable1 expires, JwtSecurityToken jwtToken, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateTokenPayload(JwtSecurityToken jwtToken, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateToken(String token, TokenValidationParameters validationParameters, SecurityToken& validatedToken) at MyApp.Web.Authentication.JwtBearer.MyAppJwtSecurityTokenHandler.ValidateToken(String securityToken, TokenValidationParameters validationParameters, SecurityToken& validatedToken) in C:\code\MyApp\aspnet-core\src\MyApp.Web.Core\Authentication\JwtBearer\MyAppJwtSecurityTokenHandler.cs:line 40 at Microsoft.AspNetCore.Authentication.JwtBearer.JwtBearerHandler.<HandleAuthenticateAsync>d__6.MoveNext() -
0
Even if this exception occurs, by default it won't cause the app to crash, it just appears in the log.
Does this exception cause a server internal error in a production environment?
Is it possible to reproduce this problem using Zero's Demo project?
-
0
It is normal if you get that error several times and your app goes back to the login page, because the angular project does several async calls to the server and if any of them return 401 client project returns to the login page. So your server can get several requests whose token was expired that's why you can get that error multiple times. But then it should go back to the login page.
-
0
Thank you for your feedback.
The problem that this exception doesn't only redirects to login. It requires resetting browser cache or closing the whole browser after re-executing app. It happens to me locally but my users in production reported the same case. App crashes for them when it's idle for sometime. I can't see this exception in log maybe because it's sort of an unhandled exception so it's swallowed up by the system.
-
0
hi kasem Is it possible to reproduce this problem in a short time? For example, 30 seconds idle?
-
0
Hi @maliming
I can't reproduce in 30seconds. It takes more time and I don't know the exact time. I feel like 30+mins
-
0
I was able to reproduce now. I launched the backend in debugging mode and I run frontend 32min later (npm start)
-
0
Attaching the validatedToken if it helps:
{{"alg":"HS256","typ":"JWT"}.{"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/nameidentifier":"9","http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name":"admin","AspNet.Identity.SecurityStamp":"SQCXBUYKAOGSPZ6AKQV2TOC5ZXE3X6NI","http://schemas.microsoft.com/ws/2008/06/identity/claims/role":["Admin"],"http://www.aspnetboilerplate.com/identity/claims/tenantId":"2","Application_StudyYearId":"4","sub":"9","jti":"400fd00d-3479-43da-82e0-e4f6c65bd538","iat":1574614578,"token_validity_key":"62d29227-3ce2-4e67-9395-3c68044d9c30","user_identifier":"9@2","token_type":"0","nbf":1574614578,"exp":1574700978,"iss":"MyApp","aud":"MyApp"}}
-
0
Hi @kasem
Is this the main cause of your problem ? At least do you think like that ? We can investigate according to this.
-
0
Hi @ismcagdas
Many cases are pointing to this one but I'm not 100% sure. It's a problem that worths investigating I think since I encounter it many times in debugging and users in production started complaining about a similar case
-
0
Hi @karen Can you share a demo project which contains that problem?
-
0
Hi @demirmusa
I'm sorry I can't provide a demo project. As I understood @ismcagdas is working to try reproducing and fixing the problem. Does this override the previous state of this ticket and demo is really blocking you now?
-
0
Solving problem would be faster if there is a demo project to reproduce it.
-
0
I have the same problem. I am restarting app and browser but nothing changed.
-
0
hi muhittincelik
Can you share a demo project which contains that problem?
-
0
i ran your last release without any code addition. core 3+angular
ran your application and npm start, open your browser and login, wait 1 day.
-
0
I simulated everyone's problem by modifying the date of the system after the user logged in to angular, but the application was as expected, the response returned http 401, and angular redirected to the login page.
INFO 2019-12-13 11:39:25,835 [5 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request starting HTTP/1.1 GET http://localhost:22742/api/services/app/Edition/GetEditions INFO 2019-12-13 11:39:25,835 [5 ] pNetCore.Cors.Infrastructure.CorsService - CORS policy execution successful. INFO 2019-12-13 11:39:25,884 [5 ] uthentication.JwtBearer.JwtBearerHandler - Failed to validate the token. Microsoft.IdentityModel.Tokens.SecurityTokenExpiredException: IDX10223: Lifetime validation failed. The token is expired. ValidTo: '12/06/2019 03:37:19', Current time: '12/13/2019 03:39:25'. at Microsoft.IdentityModel.Tokens.Validators.ValidateLifetime(Nullable`1 notBefore, Nullable`1 expires, SecurityToken securityToken, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateLifetime(Nullable`1 notBefore, Nullable`1 expires, JwtSecurityToken jwtToken, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateTokenPayload(JwtSecurityToken jwtToken, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateToken(String token, TokenValidationParameters validationParameters, SecurityToken& validatedToken) at MyCompanyName.AbpZeroTemplate.Web.Authentication.JwtBearer.AbpZeroTemplateJwtSecurityTokenHandler.ValidateToken(String securityToken, TokenValidationParameters validationParameters, SecurityToken& validatedToken) in D:\Github\volo\aspnet-zero-core\aspnet-core\src\MyCompanyName.AbpZeroTemplate.Web.Core\Authentication\JwtBearer\AbpZeroTemplateJwtSecurityTokenHandler.cs:line 40 at Microsoft.AspNetCore.Authentication.JwtBearer.JwtBearerHandler.HandleAuthenticateAsync() INFO 2019-12-13 11:39:25,884 [5 ] uthentication.JwtBearer.JwtBearerHandler - Bearer was not authenticated. Failure message: IDX10223: Lifetime validation failed. The token is expired. ValidTo: '12/06/2019 03:37:19', Current time: '12/13/2019 03:39:25'. DEBUG 2019-12-13 11:39:25,991 [56 ] HttpRequestEntityChangeSetReasonProvider - Unable to get URL from HttpRequest, fallback to null INFO 2019-12-13 11:39:25,996 [5 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request starting HTTP/1.1 GET http://localhost:22742/.well-known/openid-configuration INFO 2019-12-13 11:39:25,998 [5 ] Server4.Hosting.IdentityServerMiddleware - Invoking IdentityServer endpoint: IdentityServer4.Endpoints.DiscoveryEndpoint for /.well-known/openid-configuration INFO 2019-12-13 11:39:25,999 [5 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request finished in 3.7872000000000003ms 200 application/json; charset=UTF-8 INFO 2019-12-13 11:39:26,038 [5 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request starting HTTP/1.1 GET http://localhost:22742/.well-known/openid-configuration/jwks INFO 2019-12-13 11:39:26,041 [5 ] Server4.Hosting.IdentityServerMiddleware - Invoking IdentityServer endpoint: IdentityServer4.Endpoints.DiscoveryKeyEndpoint for /.well-known/openid-configuration/jwks INFO 2019-12-13 11:39:26,041 [5 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request finished in 3.1260000000000003ms 200 application/jwk-set+json; charset=UTF-8 INFO 2019-12-13 11:39:26,146 [20 ] uthentication.JwtBearer.JwtBearerHandler - Failed to validate the token. Microsoft.IdentityModel.Tokens.SecurityTokenInvalidSignatureException: IDX10503: Signature validation failed. Keys tried: 'Microsoft.IdentityModel.Tokens.RsaSecurityKey, KeyId: '121bf32a6b07cdc4c121fab45edfff44', InternalId: '562b04ce-676a-446b-8183-923c2425fd53'. , KeyId: 121bf32a6b07cdc4c121fab45edfff44 '. Exceptions caught: 'System.NotSupportedException: IDX10634: Unable to create the SignatureProvider. Algorithm: 'HS256', SecurityKey: 'Microsoft.IdentityModel.Tokens.RsaSecurityKey, KeyId: '121bf32a6b07cdc4c121fab45edfff44', InternalId: '562b04ce-676a-446b-8183-923c2425fd53'.' is not supported. The list of supported algorithms is available here: https://aka.ms/IdentityModel/supported-algorithms at Microsoft.IdentityModel.Tokens.CryptoProviderFactory.CreateSignatureProvider(SecurityKey key, String algorithm, Boolean willCreateSignatures) at Microsoft.IdentityModel.Tokens.CryptoProviderFactory.CreateForVerifying(SecurityKey key, String algorithm) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateSignature(Byte[] encodedBytes, Byte[] signature, SecurityKey key, String algorithm, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateSignature(String token, TokenValidationParameters validationParameters) '. token: '{"alg":"HS256","typ":"JWT"}.{"sub":"1","name":"admin","AspNet.Identity.SecurityStamp":"2NJTSQYWMBUMFV7QOQKE7FDMEG74AYSK","role":"Admin","jti":"03382578-8e96-4a12-ba83-f78055f39d35","iat":1575517039,"token_validity_key":"585e1064-5e69-41ea-9439-74dd7ab35042","user_identifier":"1","token_type":"0","nbf":1575517039,"exp":1575603439,"iss":"AbpZeroTemplate","aud":"AbpZeroTemplate"}'. at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateSignature(String token, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateToken(String token, TokenValidationParameters validationParameters, SecurityToken& validatedToken) at Microsoft.AspNetCore.Authentication.JwtBearer.JwtBearerHandler.HandleAuthenticateAsync() INFO 2019-12-13 11:39:26,146 [20 ] uthentication.JwtBearer.JwtBearerHandler - IdentityBearerIdentityServerAuthenticationJwt was not authenticated. Failure message: IDX10503: Signature validation failed. Keys tried: 'Microsoft.IdentityModel.Tokens.RsaSecurityKey, KeyId: '121bf32a6b07cdc4c121fab45edfff44', InternalId: '562b04ce-676a-446b-8183-923c2425fd53'. , KeyId: 121bf32a6b07cdc4c121fab45edfff44 '. Exceptions caught: 'System.NotSupportedException: IDX10634: Unable to create the SignatureProvider. Algorithm: 'HS256', SecurityKey: 'Microsoft.IdentityModel.Tokens.RsaSecurityKey, KeyId: '121bf32a6b07cdc4c121fab45edfff44', InternalId: '562b04ce-676a-446b-8183-923c2425fd53'.' is not supported. The list of supported algorithms is available here: https://aka.ms/IdentityModel/supported-algorithms at Microsoft.IdentityModel.Tokens.CryptoProviderFactory.CreateSignatureProvider(SecurityKey key, String algorithm, Boolean willCreateSignatures) at Microsoft.IdentityModel.Tokens.CryptoProviderFactory.CreateForVerifying(SecurityKey key, String algorithm) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateSignature(Byte[] encodedBytes, Byte[] signature, SecurityKey key, String algorithm, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateSignature(String token, TokenValidationParameters validationParameters) '. token: '{"alg":"HS256","typ":"JWT"}.{"sub":"1","name":"admin","AspNet.Identity.SecurityStamp":"2NJTSQYWMBUMFV7QOQKE7FDMEG74AYSK","role":"Admin","jti":"03382578-8e96-4a12-ba83-f78055f39d35","iat":1575517039,"token_validity_key":"585e1064-5e69-41ea-9439-74dd7ab35042","user_identifier":"1","token_type":"0","nbf":1575517039,"exp":1575603439,"iss":"AbpZeroTemplate","aud":"AbpZeroTemplate"}'. INFO 2019-12-13 11:39:26,146 [20 ] tion.IdentityServerAuthenticationHandler - IdentityBearer was not authenticated. Failure message: IDX10503: Signature validation failed. Keys tried: 'Microsoft.IdentityModel.Tokens.RsaSecurityKey, KeyId: '121bf32a6b07cdc4c121fab45edfff44', InternalId: '562b04ce-676a-446b-8183-923c2425fd53'. , KeyId: 121bf32a6b07cdc4c121fab45edfff44 '. Exceptions caught: 'System.NotSupportedException: IDX10634: Unable to create the SignatureProvider. Algorithm: 'HS256', SecurityKey: 'Microsoft.IdentityModel.Tokens.RsaSecurityKey, KeyId: '121bf32a6b07cdc4c121fab45edfff44', InternalId: '562b04ce-676a-446b-8183-923c2425fd53'.' is not supported. The list of supported algorithms is available here: https://aka.ms/IdentityModel/supported-algorithms at Microsoft.IdentityModel.Tokens.CryptoProviderFactory.CreateSignatureProvider(SecurityKey key, String algorithm, Boolean willCreateSignatures) at Microsoft.IdentityModel.Tokens.CryptoProviderFactory.CreateForVerifying(SecurityKey key, String algorithm) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateSignature(Byte[] encodedBytes, Byte[] signature, SecurityKey key, String algorithm, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateSignature(String token, TokenValidationParameters validationParameters) '. token: '{"alg":"HS256","typ":"JWT"}.{"sub":"1","name":"admin","AspNet.Identity.SecurityStamp":"2NJTSQYWMBUMFV7QOQKE7FDMEG74AYSK","role":"Admin","jti":"03382578-8e96-4a12-ba83-f78055f39d35","iat":1575517039,"token_validity_key":"585e1064-5e69-41ea-9439-74dd7ab35042","user_identifier":"1","token_type":"0","nbf":1575517039,"exp":1575603439,"iss":"AbpZeroTemplate","aud":"AbpZeroTemplate"}'. INFO 2019-12-13 11:39:26,146 [20 ] tCore.Cors.Infrastructure.CorsMiddleware - No CORS policy found for the specified request. INFO 2019-12-13 11:39:26,147 [20 ] ft.AspNetCore.Routing.EndpointMiddleware - Executing endpoint 'MyCompanyName.AbpZeroTemplate.Editions.EditionAppService.GetEditions (MyCompanyName.AbpZeroTemplate.Application)' INFO 2019-12-13 11:39:26,149 [20 ] c.Infrastructure.ControllerActionInvoker - Route matched with {area = "app", action = "GetEditions", controller = "Edition"}. Executing controller action with signature System.Threading.Tasks.Task`1[Abp.Application.Services.Dto.ListResultDto`1[MyCompanyName.AbpZeroTemplate.Editions.Dto.EditionListDto]] GetEditions() on controller MyCompanyName.AbpZeroTemplate.Editions.EditionAppService (MyCompanyName.AbpZeroTemplate.Application). WARN 2019-12-13 11:39:26,466 [20 ] Mvc.Authorization.AbpAuthorizationFilter - Abp.Authorization.AbpAuthorizationException: Current user did not login to the application! at Abp.Authorization.AuthorizationHelper.AuthorizeAsync(IEnumerable`1 authorizeAttributes) at Abp.Authorization.AuthorizationHelper.CheckPermissionsAsync(MethodInfo methodInfo, Type type) at Abp.Authorization.AuthorizationHelper.AuthorizeAsync(MethodInfo methodInfo, Type type) at Abp.AspNetCore.Mvc.Authorization.AbpAuthorizationFilter.OnAuthorizationAsync(AuthorizationFilterContext context) Abp.Authorization.AbpAuthorizationException: Current user did not login to the application! at Abp.Authorization.AuthorizationHelper.AuthorizeAsync(IEnumerable`1 authorizeAttributes) at Abp.Authorization.AuthorizationHelper.CheckPermissionsAsync(MethodInfo methodInfo, Type type) at Abp.Authorization.AuthorizationHelper.AuthorizeAsync(MethodInfo methodInfo, Type type) at Abp.AspNetCore.Mvc.Authorization.AbpAuthorizationFilter.OnAuthorizationAsync(AuthorizationFilterContext context) INFO 2019-12-13 11:39:26,466 [20 ] c.Infrastructure.ControllerActionInvoker - Authorization failed for the request at filter 'Abp.AspNetCore.Mvc.Authorization.AbpAuthorizationFilter'. INFO 2019-12-13 11:39:26,466 [20 ] .Mvc.Infrastructure.ObjectResultExecutor - Executing ObjectResult, writing value of type 'Abp.Web.Models.AjaxResponse'. INFO 2019-12-13 11:39:26,467 [20 ] c.Infrastructure.ControllerActionInvoker - Executed action MyCompanyName.AbpZeroTemplate.Editions.EditionAppService.GetEditions (MyCompanyName.AbpZeroTemplate.Application) in 317.9118ms INFO 2019-12-13 11:39:26,467 [20 ] ft.AspNetCore.Routing.EndpointMiddleware - Executed endpoint 'MyCompanyName.AbpZeroTemplate.Editions.EditionAppService.GetEditions (MyCompanyName.AbpZeroTemplate.Application)' INFO 2019-12-13 11:39:26,467 [20 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request finished in 632.0074000000001ms 401 application/json; charset=utf-8 -
0
DEBUG 2019-12-02 14:29:49,513 [24 ] HttpRequestEntityChangeSetReasonProvider - Unable to get URL from HttpRequest, fallback to null DEBUG 2019-12-02 14:29:54,580 [20 ] HttpRequestEntityChangeSetReasonProvider - Unable to get URL from HttpRequest, fallback to null DEBUG 2019-12-02 14:29:59,649 [23 ] HttpRequestEntityChangeSetReasonProvider - Unable to get URL from HttpRequest, fallback to null INFO 2019-12-02 14:30:03,276 [24 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request starting HTTP/1.1 OPTIONS http://localhost:22742/AbpUserConfiguration/GetAll?d=1575286203265 INFO 2019-12-02 14:30:03,290 [24 ] pNetCore.Cors.Infrastructure.CorsService - CORS policy execution successful. INFO 2019-12-02 14:30:03,300 [24 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request finished in 23.6981ms 204 INFO 2019-12-02 14:30:03,306 [24 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request starting HTTP/1.1 GET http://localhost:22742/AbpUserConfiguration/GetAll?d=1575286203265 application/json INFO 2019-12-02 14:30:03,306 [24 ] pNetCore.Cors.Infrastructure.CorsService - CORS policy execution successful. INFO 2019-12-02 14:32:08,624 [24 ] uthentication.JwtBearer.JwtBearerHandler - Failed to validate the token. Microsoft.IdentityModel.Tokens.SecurityTokenExpiredException: IDX10223: Lifetime validation failed. The token is expired. ValidTo: '[PII is hidden. For more details, see https://aka.ms/IdentityModel/PII.]', Current time: '[PII is hidden. For more details, see https://aka.ms/IdentityModel/PII.]'. GetCurrentLoginInformations() on controller Smart.Sessions.SessionAppService (Smart.Application). DEBUG 2019-12-02 14:32:58,968 [35 ] HttpRequestEntityChangeSetReasonProvider - Unable to get URL from HttpRequest, fallback to null DEBUG 2019-12-02 14:32:59,026 [29 ] HttpRequestEntityChangeSetReasonProvider - Unable to get URL from HttpRequest, fallback to null INFO 2019-12-02 14:32:59,150 [35 ] .Mvc.Infrastructure.ObjectResultExecutor - Executing ObjectResult, writing value of type 'Abp.Web.Models.AjaxResponse'. INFO 2019-12-02 14:32:59,177 [35 ] c.Infrastructure.ControllerActionInvoker - Executed action Smart.Sessions.SessionAppService.GetCurrentLoginInformations (Smart.Application) in 242.1742ms INFO 2019-12-02 14:32:59,177 [35 ] ft.AspNetCore.Routing.EndpointMiddleware - Executed endpoint 'Smart.Sessions.SessionAppService.GetCurrentLoginInformations (Smart.Application)' INFO 2019-12-02 14:32:59,178 [35 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request finished in 48856.624800000005ms 200 application/json; charset=utf-8 DEBUG 2019-12-02 14:32:59,223 [20 ] HttpRequestEntityChangeSetReasonProvider - Unable to get URL from HttpRequest, fallback to null DEBUG 2019-12-02 14:33:04,122 [39 ] HttpRequestEntityChangeSetReasonProvider - Unable to get URL from HttpRequest, fallback to null INFO 2019-12-02 14:33:07,790 [39 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request starting HTTP/1.1 OPTIONS http://localhost:22742/AbpUserConfiguration/GetAll?d=1575286387785 INFO 2019-12-02 14:33:07,792 [39 ] pNetCore.Cors.Infrastructure.CorsService - CORS policy execution successful. INFO 2019-12-02 14:33:07,796 [39 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request finished in 4.7914ms 204 INFO 2019-12-02 14:33:07,823 [39 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request starting HTTP/1.1 GET http://localhost:22742/AbpUserConfiguration/GetAll?d=1575286387785 application/json INFO 2019-12-02 14:33:07,823 [39 ] pNetCore.Cors.Infrastructure.CorsService - CORS policy execution successful. DEBUG 2019-12-02 14:36:13,492 [29 ] HttpRequestEntityChangeSetReasonProvider - Unable to get URL from HttpRequest, fallback to null INFO 2019-12-02 14:36:13,494 [39 ] uthentication.JwtBearer.JwtBearerHandler - Failed to validate the token. Microsoft.IdentityModel.Tokens.SecurityTokenExpiredException: IDX10223: Lifetime validation failed. The token is expired. ValidTo: '[PII is hidden. For more details, see https://aka.ms/IdentityModel/PII.]', Current time: '[PII is hidden. For more details, see https://aka.ms/IdentityModel/PII.]'. at Microsoft.IdentityModel.Tokens.Validators.ValidateLifetime(Nullable`1 notBefore, Nullable`1 expires, SecurityToken securityToken, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateLifetime(Nullable`1 notBefore, Nullable`1 expires, JwtSecurityToken jwtToken, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateTokenPayload(JwtSecurityToken jwtToken, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateToken(String token, TokenValidationParameters validationParameters, SecurityToken& validatedToken) at Smart.Web.Authentication.JwtBearer.SmartJwtSecurityTokenHandler.ValidateToken(String securityToken, TokenValidationParameters validationParameters, SecurityToken& validatedToken) in D:\Fide\Projeler\Smart Inventory V8.0.0\Core\src\Smart.Web.Core\Authentication\JwtBearer\SmartJwtSecurityTokenHandler.cs:line 40 at Microsoft.AspNetCore.Authentication.JwtBearer.JwtBearerHandler.HandleAuthenticateAsync() INFO 2019-12-02 14:36:13,495 [39 ] uthentication.JwtBearer.JwtBearerHandler - Bearer was not authenticated. Failure message: IDX10223: Lifetime validation failed. The token is expired. ValidTo: '[PII is hidden. For more details, see https://aka.ms/IdentityModel/PII.]', Current time: '[PII is hidden. For more details, see https://aka.ms/IdentityModel/PII.]'. INFO 2019-12-02 14:36:13,495 [39 ] ft.AspNetCore.Routing.EndpointMiddleware - Executing endpoint 'Abp.AspNetCore.Mvc.Controllers.AbpUserConfigurationController.GetAll (Abp.AspNetCore)' DEBUG 2019-12-02 14:36:26,124 [43 ] HttpRequestEntityChangeSetReasonProvider - Unable to get URL from HttpRequest, fallback to null INFO 2019-12-02 14:36:33,926 [39 ] c.Infrastructure.ControllerActionInvoker - Route matched with {action = "GetAll", controller = "AbpUserConfiguration", area = ""}. Executing controller action with signature System.Threading.Tasks.Task`1[Microsoft.AspNetCore.Mvc.JsonResult] GetAll() on controller Abp.AspNetCore.Mvc.Controllers.AbpUserConfigurationController (Abp.AspNetCore). DEBUG 2019-12-02 14:36:35,257 [44 ] HttpRequestEntityChangeSetReasonProvider - Unable to get URL from HttpRequest, fallback to null DEBUG 2019-12-02 14:36:42,761 [42 ] HttpRequestEntityChangeSetReasonProvider - Unable to get URL from HttpRequest, fallback to null INFO 2019-12-02 14:36:46,256 [20 ] tonsoftJson.NewtonsoftJsonResultExecutor - Executing JsonResult, writing value of type 'Abp.Web.Models.AjaxResponse'. INFO 2019-12-02 14:36:46,298 [6 ] c.Infrastructure.ControllerActionInvoker - Executed action Abp.AspNetCore.Mvc.Controllers.AbpUserConfigurationController.GetAll (Abp.AspNetCore) in 12370.986700000001ms INFO 2019-12-02 14:36:46,298 [6 ] ft.AspNetCore.Routing.EndpointMiddleware - Executed endpoint 'Abp.AspNetCore.Mvc.Controllers.AbpUserConfigurationController.GetAll (Abp.AspNetCore)' INFO 2019-12-02 14:36:46,298 [6 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request finished in 218475.90730000002ms 200 application/json; charset=utf-8 INFO 2019-12-02 14:36:46,355 [29 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request starting HTTP/1.1 OPTIONS http://localhost:22742/api/services/app/Session/GetCurrentLoginInformations INFO 2019-12-02 14:36:46,355 [29 ] pNetCore.Cors.Infrastructure.CorsService - CORS policy execution successful. INFO 2019-12-02 14:36:46,356 [29 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request finished in 1.2573ms 204 INFO 2019-12-02 14:36:46,362 [29 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request starting HTTP/1.1 GET http://localhost:22742/api/services/app/Session/GetCurrentLoginInformations INFO 2019-12-02 14:36:46,363 [29 ] pNetCore.Cors.Infrastructure.CorsService - CORS policy execution successful. DEBUG 2019-12-02 14:37:26,264 [36 ] HttpRequestEntityChangeSetReasonProvider - Unable to get URL from HttpRequest, fallback to null INFO 2019-12-02 14:37:26,266 [29 ] uthentication.JwtBearer.JwtBearerHandler - Failed to validate the token. Microsoft.IdentityModel.Tokens.SecurityTokenExpiredException: IDX10223: Lifetime validation failed. The token is expired. ValidTo: '[PII is hidden. For more details, see https://aka.ms/IdentityModel/PII.]', Current time: '[PII is hidden. For more details, see https://aka.ms/IdentityModel/PII.]'. at Microsoft.IdentityModel.Tokens.Validators.ValidateLifetime(Nullable`1 notBefore, Nullable`1 expires, SecurityToken securityToken, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateLifetime(Nullable`1 notBefore, Nullable`1 expires, JwtSecurityToken jwtToken, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateTokenPayload(JwtSecurityToken jwtToken, TokenValidationParameters validationParameters) at System.IdentityModel.Tokens.Jwt.JwtSecurityTokenHandler.ValidateToken(String token, TokenValidationParameters validationParameters, SecurityToken& validatedToken) at Smart.Web.Authentication.JwtBearer.SmartJwtSecurityTokenHandler.ValidateToken(String securityToken, TokenValidationParameters validationParameters, SecurityToken& validatedToken) in D:\Fide\Projeler\Smart Inventory V8.0.0\Core\src\Smart.Web.Core\Authentication\JwtBearer\SmartJwtSecurityTokenHandler.cs:line 40 at Microsoft.AspNetCore.Authentication.JwtBearer.JwtBearerHandler.HandleAuthenticateAsync() INFO 2019-12-02 14:37:26,268 [29 ] uthentication.JwtBearer.JwtBearerHandler - Bearer was not authenticated. Failure message: IDX10223: Lifetime validation failed. The token is expired. ValidTo: '[PII is hidden. For more details, see https://aka.ms/IdentityModel/PII.]', Current time: '[PII is hidden. For more details, see https://aka.ms/IdentityModel/PII.]'. INFO 2019-12-02 14:37:26,269 [29 ] ft.AspNetCore.Routing.EndpointMiddleware - Executing endpoint 'Smart.Sessions.SessionAppService.GetCurrentLoginInformations (Smart.Application)' INFO 2019-12-02 14:37:26,275 [29 ] c.Infrastructure.ControllerActionInvoker - Route matched with {area = "app", action = "GetCurrentLoginInformations", controller = "Session"}. Executing controller action with signature System.Threading.Tasks.Task`1[Smart.Sessions.Dto.GetCurrentLoginInformationsOutput] GetCurrentLoginInformations() on controller Smart.Sessions.SessionAppService (Smart.Application). INFO 2019-12-02 14:37:26,581 [44 ] .Mvc.Infrastructure.ObjectResultExecutor - Executing ObjectResult, writing value of type 'Abp.Web.Models.AjaxResponse'. INFO 2019-12-02 14:37:26,582 [44 ] c.Infrastructure.ControllerActionInvoker - Executed action Smart.Sessions.SessionAppService.GetCurrentLoginInformations (Smart.Application) in 306.5673ms INFO 2019-12-02 14:37:26,582 [44 ] ft.AspNetCore.Routing.EndpointMiddleware - Executed endpoint 'Smart.Sessions.SessionAppService.GetCurrentLoginInformations (Smart.Application)' INFO 2019-12-02 14:37:26,583 [44 ] Microsoft.AspNetCore.Hosting.Diagnostics - Request finished in 40220.9236ms 200 application/json; charset=utf-8 DEBUG 2019-12-02 14:37:31,499 [48 ] HttpRequestEntityChangeSetReasonProvider - Unable to get URL from HttpRequest, fallback to null -
0
-
0
Hi @muhittincelik is that ok if I connect your pc and check that error via teamviewer?