Activities of "Bernard"
Hi Ismail,
I finally found the good way :
// Retrieve required permissions from appsettings string[] initialScopes = configuration.GetValue<string>("DownstreamApi:Scopes")?.Split(' ');
var authenticationBuilder = services.AddAuthentication(options => { options.DefaultScheme = "OpenIdConnect"; options.DefaultChallengeScheme = "AzureAd";
if (bool.Parse(configuration["Authentication:OpenId:IsEnabled"])) { if (bool.Parse(configuration["Authentication:AllowSocialLoginSettingsPerTenant"])) { services.AddSingleton<IOptionsMonitor<OpenIdConnectOptions>, TenantBasedOpenIdConnectOptions>(); }
authenticationBuilder.AddOpenIdConnect(options =>
{
options.ClientId = configuration["Authentication:OpenId:ClientId"];
options.Authority = configuration["Authentication:OpenId:Authority"];
options.SignedOutRedirectUri = configuration["App:WebSiteRootAddress"] + "Account/Logout";
options.ResponseType = configuration["Authentication:OpenId:ResponseType"];
options.TokenValidationParameters = new TokenValidationParameters()
{
ValidateIssuer = bool.Parse(configuration["Authentication:OpenId:ValidateIssuer"])
};
options.Events.OnTokenValidated = context =>
{
var jsonClaimMappings = new List<JsonClaimMap>();
configuration.GetSection("Authentication:OpenId:ClaimsMapping").Bind(jsonClaimMappings);
context.AddMappedClaims(jsonClaimMappings);
return Task.FromResult(0);
};
var clientSecret = configuration["Authentication:OpenId:ClientSecret"];
if (!clientSecret.IsNullOrEmpty())
{
options.ClientSecret = clientSecret;
}
})**.AddMicrosoftIdentityWebApp(options =>
{
options.ClientId = configuration["Authentication:AzureAd:ClientId"];
options.Instance= configuration["Authentication:AzureAd:Instance"];
options.TenantId = configuration["Authentication:AzureAd:TenantId"];
options.SignedOutRedirectUri = configuration["App:WebSiteRootAddress"] + "Account/Logout";
var clientSecret = configuration["Authentication:AzureAd:ClientSecret"];
if (!clientSecret.IsNullOrEmpty())
{
options.ClientSecret = clientSecret;
}
}, null, "AzureAd")
.EnableTokenAcquisitionToCallDownstreamApi(initialScopes)
.AddMicrosoftGraph(configuration.GetSection("DownstreamApi"))
.AddInMemoryTokenCaches();**
};
//MS Graph Authentification services.AddAuthentication().AddMicrosoftIdentityWebApp(configuration.GetSection("AzureAd")) .EnableTokenAcquisitionToCallDownstreamApi(configuration.GetValue<string>("DownstreamApi:Scopes")?.Split(' ')) .AddMicrosoftGraph(configuration.GetSection("DownstreamApi")) .AddInMemoryTokenCaches();
Same issue
I follow your example like :
var authenticationBuilder = services.AddAuthentication();
if (bool.Parse(configuration["Authentication:OpenId:IsEnabled"]))
{
if (bool.Parse(configuration["Authentication:AllowSocialLoginSettingsPerTenant"]))
{
services.AddSingleton<IOptionsMonitor<OpenIdConnectOptions>, TenantBasedOpenIdConnectOptions>();
}
authenticationBuilder.AddOpenIdConnect(options =>
{
options.ClientId = configuration["Authentication:OpenId:ClientId"];
options.Authority = configuration["Authentication:OpenId:Authority"];
options.SignedOutRedirectUri = configuration["App:WebSiteRootAddress"] + "Account/Logout";
options.ResponseType = configuration["Authentication:OpenId:ResponseType"];
options.TokenValidationParameters = new TokenValidationParameters()
{
ValidateIssuer = bool.Parse(configuration["Authentication:OpenId:ValidateIssuer"])
};
options.Events.OnTokenValidated = context =>
{
var jsonClaimMappings = new List<JsonClaimMap>();
configuration.GetSection("Authentication:OpenId:ClaimsMapping").Bind(jsonClaimMappings);
context.AddMappedClaims(jsonClaimMappings);
return Task.FromResult(0);
};
var clientSecret = configuration["Authentication:OpenId:ClientSecret"];
if (!clientSecret.IsNullOrEmpty())
{
options.ClientSecret = clientSecret;
}
});
};
authenticationBuilder.AddMicrosoftIdentityWebApp(configuration.GetSection("AzureAd"))
.EnableTokenAcquisitionToCallDownstreamApi(configuration.GetValue<string>("DownstreamApi:Scopes")?.Split(' '))
.AddMicrosoftGraph(configuration.GetSection("DownstreamApi"))
.AddInMemoryTokenCaches();
but it cause issue
An error occurred while starting the application. InvalidOperationException: Scheme already exists: OpenIdConnect
Microsoft.AspNetCore.Authentication.AuthenticationOptions.AddScheme(string name, Action<AuthenticationSchemeBuilder> configureBuilder) ComponentActivatorException: ComponentActivator: could not instantiate Microsoft.AspNetCore.Authentication.AuthenticationSchemeProvider
Castle.MicroKernel.ComponentActivator.DefaultComponentActivator.CreateInstanceCore(ConstructorCandidate constructor, object[] arguments, Type implType)
InvalidOperationException: Scheme already exists: OpenIdConnect
Microsoft.AspNetCore.Authentication.AuthenticationOptions.AddScheme(string name, Action<AuthenticationSchemeBuilder> configureBuilder)
Microsoft.Extensions.Options.OptionsFactory<TOptions>.Create(string name)
Microsoft.Extensions.Options.UnnamedOptionsManager<TOptions>.get_Value()
Microsoft.AspNetCore.Authentication.AuthenticationSchemeProvider..ctor(IOptions<AuthenticationOptions> options, IDictionary<string, AuthenticationScheme> schemes)
lambda_method47(Closure , object[] )
Castle.Core.Internal.ReflectionUtil.Instantiate(ConstructorInfo ctor, object[] ctorArgs)
Castle.Core.Internal.ReflectionUtil.Instantiate<TBase>(Type subtypeofTBase, object[] ctorArgs)
Castle.MicroKernel.ComponentActivator.DefaultComponentActivator.CreateInstanceCore(ConstructorCandidate constructor, object[] arguments, Type implType)
Hi
No, I not able to call AddMicrosoftIdentityWebApp And Openconnect because each uses the same scheme
Hi,
Any idea ? For having 2 schemes when Connecting ?
I think it should be something like this : https://stackoverflow.com/questions/49694383/use-multiple-jwt-bearer-authentication but for Openconnect
Hi ismail,
Thks
Hi I send you detail by email did you receive it ?
Hi
I see it support but you must change manifest and workaround security So I prefer keep manually
Thanks
Hi,
After changing this value
var emailClaim = claims.FirstOrDefault(c => c.Type == "unique_name");
to
var emailClaim = claims.FirstOrDefault(c => c.Type == "preferred_username");
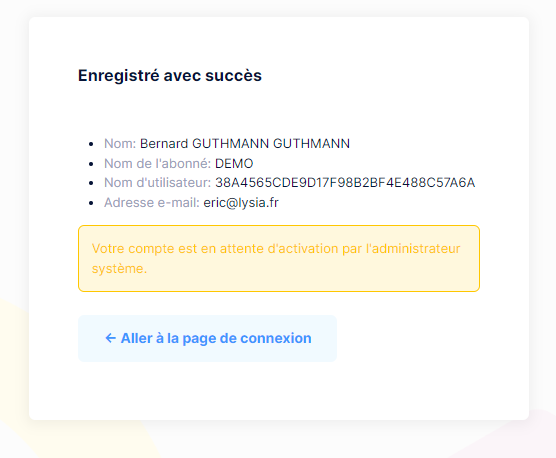
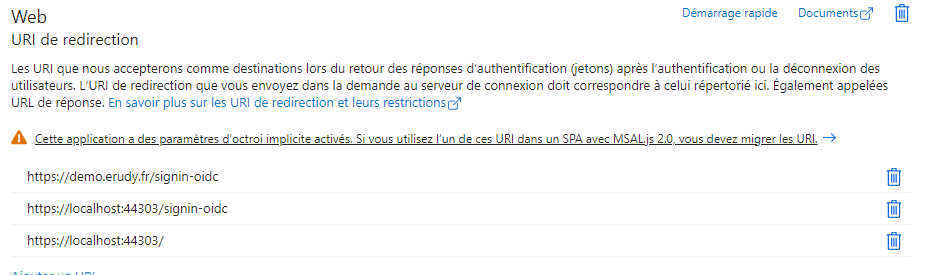
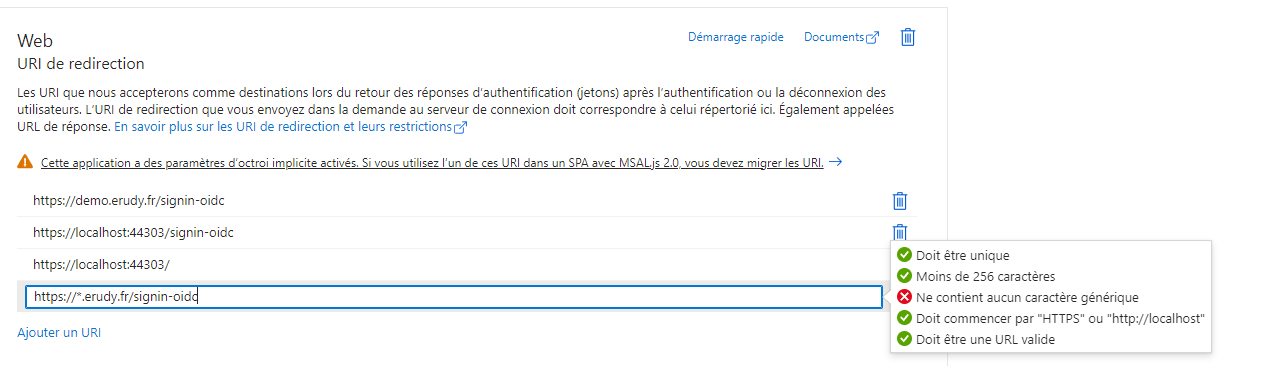
But i think we **must always **add the tenant subdomain manually to make the openconnectId work ?
Hi,
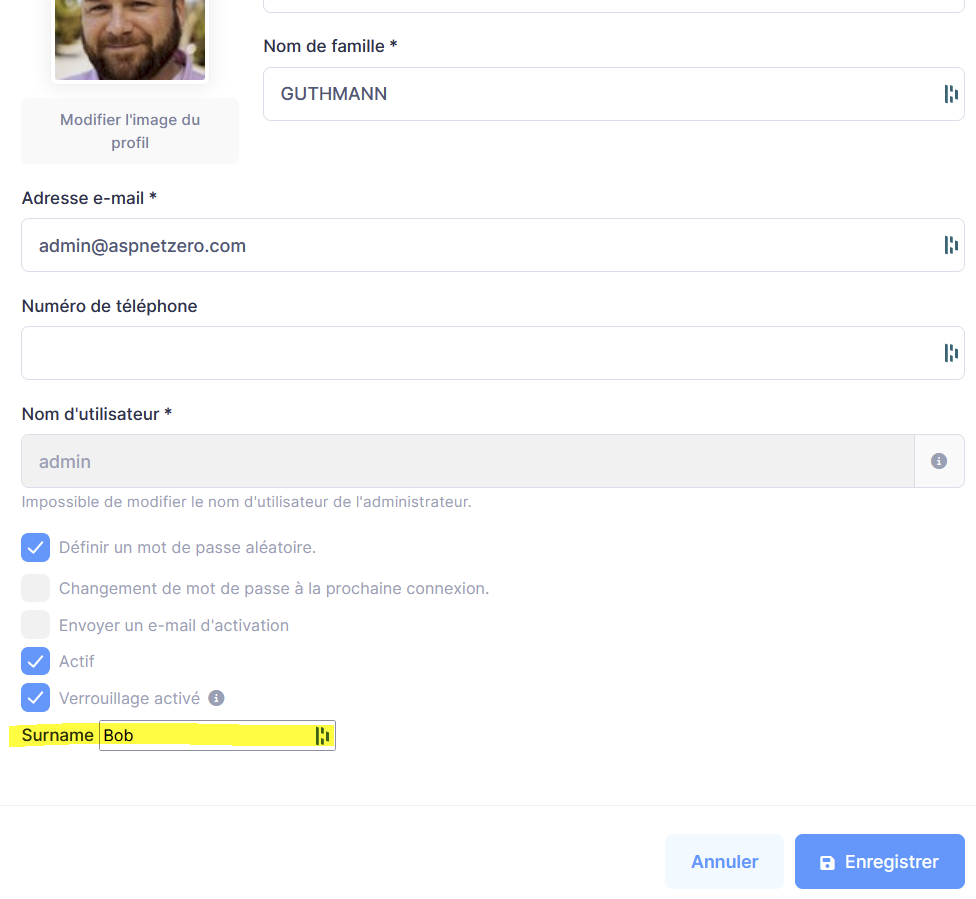
I would like to save it also.
Like
I’d like to display the good control combobox Date String I think on looping with switch case on type
@foreach (var item in Model.DynamicProperties)
{
<div class="mb-5">
<label for="edp-create-modal-dynamicPropertyId" class="form-label">@item.PropertyName</label>
@switch (item.InputType.Name)
{
case "COMBOBOX" :
// code block
break;
case "SINGLE_LINE_STRING":
// code block
break;
case "DATETIME":
// code block
break;
}
</div>